Ransomware: A Growing Threat and How to Protect Yourself
Ransomware, a malicious software encrypting data and demanding a ransom for its release, poses a significant threat to individuals and businesses. High-profile attacks like WannaCry and Bad Rabbit highlight the devastating consequences. The annual growth rate of ransomware incidents is a staggering 350%, emphasizing the urgent need for robust preventative measures.
How Ransomware Works
Ransomware operates by infiltrating a computer system, encrypting files, and blocking access until a ransom is paid. Cybercriminals often impose deadlines, threatening permanent data loss if the ransom isn't met. However, paying the ransom offers no guarantee of data recovery, as criminals are not bound by any ethical code. Prevention is far more effective than reacting to an attack.
Spread of Ransomware
Ransomware spreads through various methods, constantly evolving to bypass security measures. Targeted attacks frequently leverage phishing emails, while poorly secured remote access services (RDP, VPN) are increasingly exploited. The rise of "ransomware-as-a-service" on the dark web further fuels the problem, providing readily available tools for malicious actors. Attacks on service providers are also becoming common, allowing widespread infection of numerous victims simultaneously. Compromised web-based security management or backup consoles can enable attackers to disable protections and delete backups, making preventative measures crucial.
Types of Ransomware Attacks
Several ransomware types exist, all united by the demand for a ransom:
- Crypto Malware: This insidious form encrypts data, often going undetected for extended periods. It can be spread through malicious email attachments or website scripts.
- Lockers: Primarily targeting Android devices, these programs completely block file access, often bundled with illegally downloaded software.
- Scareware: Disguised as antivirus or cleaning tools, this malware locks computers or displays pop-up messages demanding payment for fabricated services.
- Doxware: This type threatens to publish stolen data online unless a ransom is paid.
- Mobile Ransomware: Since 2014, mobile devices have also become targets, with malicious apps blocking access until a ransom is paid.
Notable Ransomware Attacks
Several infamous ransomware attacks illustrate the scale of the threat:
- Locky (2016): Spread through malicious email attachments, encrypting over 150 file types.
- WannaCry (2017): Infected over 230,000 computers globally, causing billions in damages.
- Bad Rabbit (2017): Spread through infected websites, using compromised Adobe Flash as a vector.
- Ryuk: Targeted numerous newspapers, encrypting files with an unbreakable code.
- Baltimore Ransomware (2019): Infected the Baltimore city network, causing significant financial losses.
Mac Ransomware Vulnerability
While less common, Macs are not immune to ransomware attacks. The KeRanger attack in 2016 demonstrated this vulnerability. Maintaining strong security practices remains vital for Mac users.
Preventing Ransomware Attacks
Effective ransomware prevention involves multiple layers of defense:
- Install comprehensive antivirus software: A robust solution like MacKeeper can detect and neutralize threats.
- Regular software updates: Keep your software and operating system current to patch security vulnerabilities.
- Caution with email attachments: Avoid opening attachments from unknown or untrusted sources.
- Disable macros unless absolutely necessary: Exercise extreme caution before enabling macros in documents.
- Regular data backups: Maintain backups on external drives or cloud services to enable easy recovery.
- Utilize cloud services: Cloud storage provides version history and reduces the impact of ransomware.
- Implement two-factor authentication (2FA): Strengthen the security of your accounts.
- Follow Apple's security recommendations: Configure your system to only allow apps from identified developers.

Should You Pay the Ransom?
Authorities strongly advise against paying ransoms. Paying encourages further attacks and provides no guarantee of data recovery. Prevention is the most effective strategy. MacKeeper can help assess your system's security and identify potential vulnerabilities. Don't become a victim – proactively protect your data.
The above is the detailed content of What is Ransomware?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undress AI Tool
Undress images for free

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 Listen to Long Audio Messages Easier on iPhone with This Trick
Jun 23, 2025 am 09:44 AM
Listen to Long Audio Messages Easier on iPhone with This Trick
Jun 23, 2025 am 09:44 AM
Have you ever received a long audio message on your iPhone and while listening, the screen turns off, interrupting the playback and forcing you to start over? It's pretty frustrating, isn't it?Next time you receive a lengthy voice message on your iPh
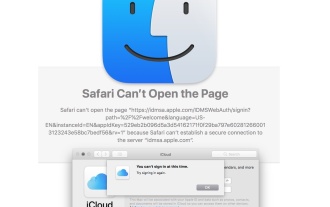 Fix iCloud Errors & “Can’t Establish Secure Connection with idmsa.apple.com” on MacOS Sierra & High Sierra
Jun 22, 2025 am 10:06 AM
Fix iCloud Errors & “Can’t Establish Secure Connection with idmsa.apple.com” on MacOS Sierra & High Sierra
Jun 22, 2025 am 10:06 AM
Some users of Mac computers running MacOS Sierra and MacOS High Sierra have reported issues when trying to log in to an Apple ID or iCloud via System Preferences, as well as problems accessing iCloud.com using Safari. In addition, Safari fails to loa
 Data Breach Reports Archive — 2017
Jun 24, 2025 am 09:51 AM
Data Breach Reports Archive — 2017
Jun 24, 2025 am 09:51 AM
In this blog post, we’ve gathered the 22 most significant breaches that happened back in 2017. All of the reports were conducted by Chris Vickery — a data breach hunter, who had partnered with MacKeeper to provide repor
 7 of the Best iOS 16 Features to Check Out Right Away
Jun 22, 2025 am 09:56 AM
7 of the Best iOS 16 Features to Check Out Right Away
Jun 22, 2025 am 09:56 AM
iOS 16 is now available for iPhone users, offering a solid update packed with practical features you're sure to enjoy.The most noticeable and exciting addition is the ability to personalize your lock screen. However, there are also plenty of smaller
 How to Make a MacOS Monterey Boot Installer Drive
Jun 24, 2025 am 09:10 AM
How to Make a MacOS Monterey Boot Installer Drive
Jun 24, 2025 am 09:10 AM
Some Mac users utilize bootable USB drives to install or upgrade to macOS Monterey. If you're looking to create a bootable macOS Monterey installer drive, we’ll guide you through the steps.This method is typically intended for advanced users who want
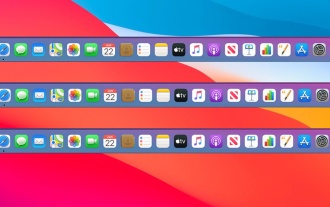 Can I Show the Dock on All Screens on Mac? Using Dock on Different Displays in macOS
Jul 03, 2025 am 09:30 AM
Can I Show the Dock on All Screens on Mac? Using Dock on Different Displays in macOS
Jul 03, 2025 am 09:30 AM
If you're using a Mac with multiple monitors, you might be curious about how to display the Dock on all screens or whether it's possible to add a Dock to secondary displays.The good news is that you can configure the Dock to appear on any screen conn
 How to Remove Old Devices from Apple ID on Mac
Jul 07, 2025 am 09:08 AM
How to Remove Old Devices from Apple ID on Mac
Jul 07, 2025 am 09:08 AM
If you've owned multiple Apple devices over the years, you might find yourself in a situation where some of those older Macs, iPhones, iPads, or other Apple hardware have been sold, given away, or traded. No matter how they left your possession, it's
 How to Play Fortnite on Mac with FnMacAssistant & Sideloadly
Jul 05, 2025 am 09:21 AM
How to Play Fortnite on Mac with FnMacAssistant & Sideloadly
Jul 05, 2025 am 09:21 AM
Fortnite is once again available for iPhone and iPad users, bringing joy to many gamers. However, there's still no official version for Mac (at least not yet). Despite that, Apple Silicon Mac owners aren’t completely out of luck—you can run the iOS/i






