How to get component_verify_ticket in EasyWechat 5.5 version?
Apr 01, 2025 am 06:06 AM
Get Component Verify Ticket in EasyWechat version 5.5
When using EasyWechat to develop a third-party WeChat platform, obtaining component_verify_ticket is a crucial step. The Ticket is a key credential for third-party platforms to perform authorization and follow-up operations. EasyWechat version 5.5 does not directly provide a function to obtain the Ticket, and developers need to handle events pushed by the WeChat server by themselves.
This article will guide you how to get and use component_verify_ticket in EasyWechat 5.5:
Server URL configuration: In the background of the third-party platform of WeChat public platform, correctly configure the server URL and token. This URL is the receiving address of the WeChat server push event.
Event reception handler: Write a program to listen to the URL and receive events pushed by the WeChat server. EasyWechat provides an event handling mechanism, you need to register an event handler and handle events containing
component_verify_ticket(usually located inticketfield).Storage
component_verify_ticket: After receivingcomponent_verify_ticket, be sure to store it, such as a database or file cache. Remember, this Ticket has an expiration date and needs to be updated regularly.Use
component_verify_ticket: After obtainingcomponent_verify_ticket, you can use other functions provided by EasyWechat, such as obtaining authorization codes, creating authorizations, etc. EasyWechat will perform the corresponding operation based oncomponent_verify_ticketyou stored.
Complete the above steps and successfully obtain and utilize component_verify_ticket in EasyWechat 5.5. Please refer to the official EasyWechat documentation for an in-depth understanding of event handling mechanisms and API usage methods. Remember, it is crucial to safely store component_verify_ticket to prevent leakage.
The above is the detailed content of How to get component_verify_ticket in EasyWechat 5.5 version?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undress AI Tool
Undress images for free

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 How to correctly handle this pointing in a closure?
May 21, 2025 pm 09:15 PM
How to correctly handle this pointing in a closure?
May 21, 2025 pm 09:15 PM
The methods to correctly handle this pointing in JavaScript closures include: 1. Use arrow functions, 2. Use bind methods, 3. Use variables to save this. These methods ensure that this intrinsic function correctly points to the context of the external function.
 The latest news APP ranking recommendation in the currency circle (authoritative release in 2025)
Apr 21, 2025 pm 09:33 PM
The latest news APP ranking recommendation in the currency circle (authoritative release in 2025)
Apr 21, 2025 pm 09:33 PM
The best cryptocurrency trading and analysis platforms include: 1. OKX: the world's number one in trading volume, supports multiple transactions, provides AI market analysis and on-chain data monitoring. 2. Binance: The world's largest exchange, providing in-depth market conditions and new currency first-time offerings. 3. Sesame Open Door: Known for spot trading and OTC channels, it provides automated trading strategies. 4. CoinMarketCap: an authoritative market data platform, covering 20,000 currencies. 5. CoinGecko: Known for community sentiment analysis, it provides DeFi and NFT trend monitoring. 6. Non-small account: a domestic market platform, providing analysis of linkage between A-shares and currency markets. 7. On-chain Finance: Focus on blockchain news and update in-depth reports every day. 8. Golden Finance: 24 small
 What is cross-compilation in C?
Apr 28, 2025 pm 08:21 PM
What is cross-compilation in C?
Apr 28, 2025 pm 08:21 PM
Cross-compilation in C refers to compiling an executable file or library that can run on another platform on one platform. 1) Cross-compilation requires the use of a special cross-compiler, such as GCC or Clang variants. 2) Setting up a cross-compilation environment can use Docker to manage toolchains to improve repeatability and portability. 3) When cross-compiling, pay attention to code optimization options, such as -O2, -O3 or -Os, to balance performance and file size.
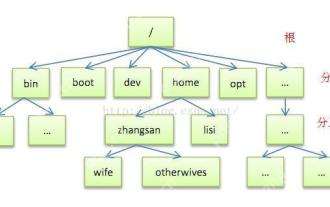 Detailed introduction to each directory of Linux and each directory (reprinted)
May 22, 2025 pm 07:54 PM
Detailed introduction to each directory of Linux and each directory (reprinted)
May 22, 2025 pm 07:54 PM
[Common Directory Description] Directory/bin stores binary executable files (ls, cat, mkdir, etc.), and common commands are generally here. /etc stores system management and configuration files/home stores all user files. The root directory of the user's home directory is the basis of the user's home directory. For example, the home directory of the user user is /home/user. You can use ~user to represent /usr to store system applications. The more important directory /usr/local Local system administrator software installation directory (install system-level applications). This is the largest directory, and almost all the applications and files to be used are in this directory. /usr/x11r6?Directory for storing x?window/usr/bin?Many
 TikTok web version entrance login link address https TikTok web version entrance website free
May 22, 2025 pm 04:24 PM
TikTok web version entrance login link address https TikTok web version entrance website free
May 22, 2025 pm 04:24 PM
The login portal for the Douyin web version is https://www.douyin.com/. The login steps include: 1. Open the browser; 2. Enter the URL https://www.douyin.com/; 3. Click the "Login" button and select the login method; 4. Enter the account password; 5. Complete login. The web version provides functions such as browsing, searching, interaction, uploading videos and personal homepage management, and has advantages such as large-screen experience, multi-tasking, convenient account management and data statistics.
 What does java middleware mean? Definition and typical applications of middleware
May 28, 2025 pm 05:51 PM
What does java middleware mean? Definition and typical applications of middleware
May 28, 2025 pm 05:51 PM
Java middleware is a software that connects operating systems and application software, providing general services to help developers focus on business logic. Typical applications include: 1. Web server (such as Tomcat and Jetty), which handles HTTP requests; 2. Message queue (such as Kafka and RabbitMQ), which handles asynchronous communication; 3. Transaction management (such as SpringTransaction), which ensures data consistency; 4. ORM framework (such as Hibernate and MyBatis), which simplifies database operations.
 Are these C2C transactions in Binance risky?
Apr 30, 2025 pm 06:54 PM
Are these C2C transactions in Binance risky?
Apr 30, 2025 pm 06:54 PM
Binance C2C transactions allow users to buy and sell cryptocurrencies directly, and pay attention to the risks of counterparty, payment and price fluctuations. Choosing high-credit users and secure payment methods can reduce risks.
 How to implement style reuse in CSS?
May 21, 2025 pm 08:57 PM
How to implement style reuse in CSS?
May 21, 2025 pm 08:57 PM
The methods to implement style reuse in CSS are: 1. Use class selector, 2. Use BEM naming convention, and 3. Use CSS preprocessor. Through these methods, the amount of code can be reduced, maintainability and consistency can be improved. For example, using a class selector can apply the same style to multiple elements, while BEM and preprocessors provide more advanced ways of multiplexing and organization.






