 System Tutorial
System Tutorial
 Windows Series
Windows Series
 【ES 3rd Anniversary】Windows-chrome installation of Elasticsearch-head plug-in
【ES 3rd Anniversary】Windows-chrome installation of Elasticsearch-head plug-in
【ES 3rd Anniversary】Windows-chrome installation of Elasticsearch-head plug-in
May 22, 2025 pm 07:42 PMDownload the zip file of elasticsearch-head plugin via the following link:
Link: http://m.miracleart.cn/link/f7084c8dc72521fe9b1cd695464554a2
Extraction code: 8888
Installation method
Method 1: Install through Google Chrome
First, open Google Chrome, click on the "More Tools" option in the upper right corner, and select "Extensions".
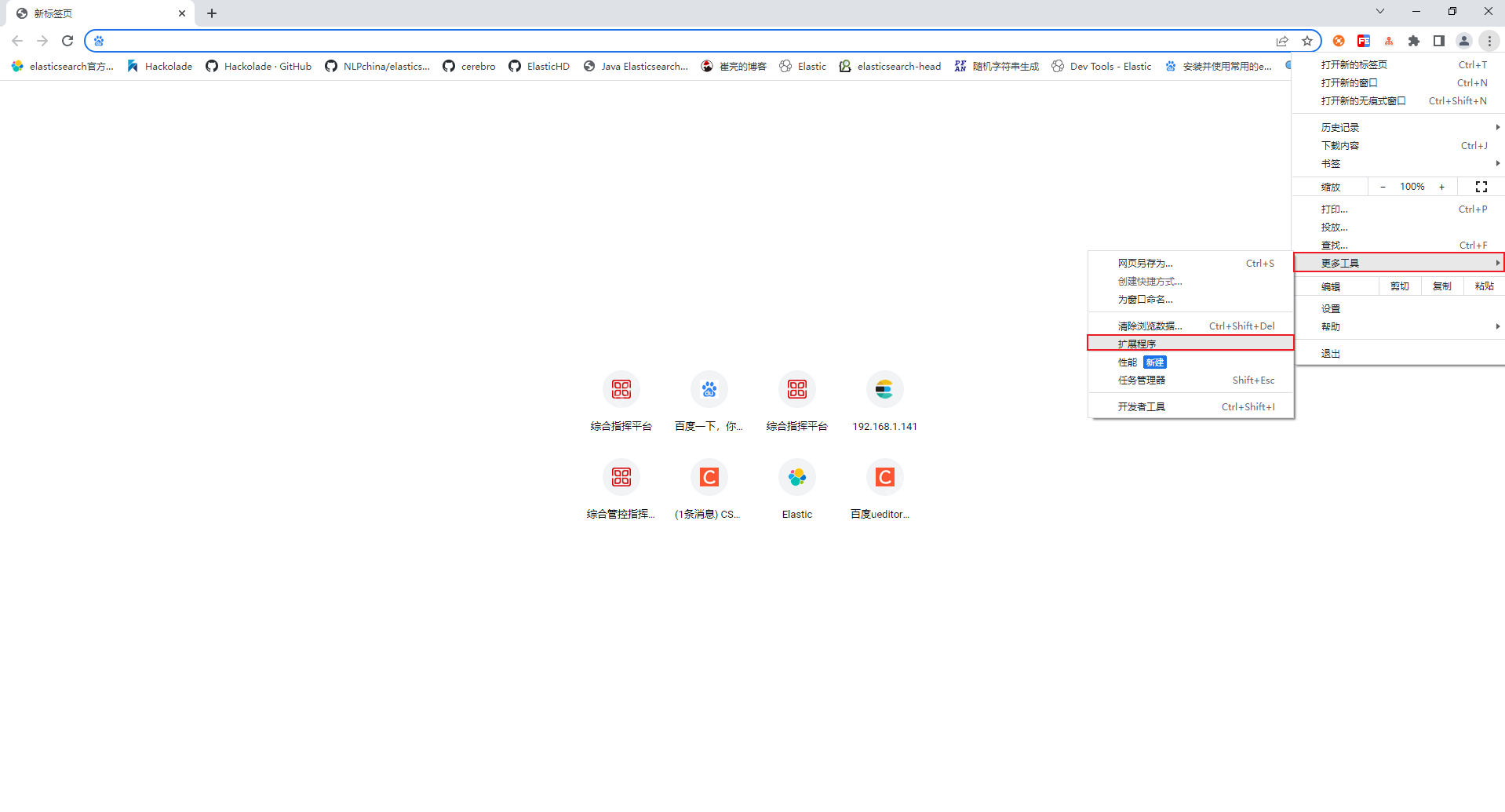
Unzip the downloaded es-head.zip file, find the third-party plug-in file with the suffix .crx, and change its suffix to .rar, and then unzip it again to get a folder.
After entering the extension page, open the developer mode, then click "Load the unzipped extension", select the folder you just unzipped, click "OK" and confirm adding the extension.
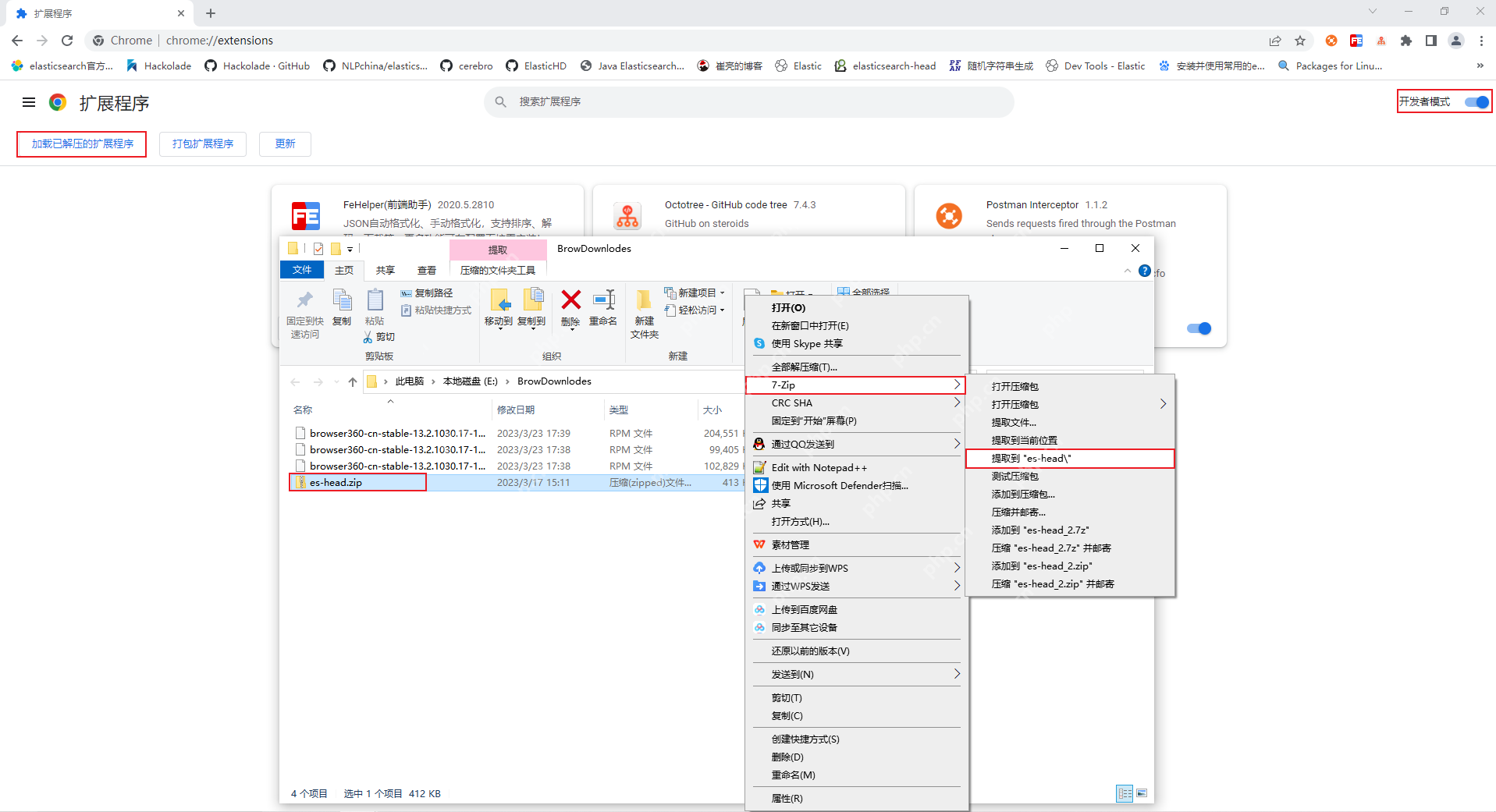
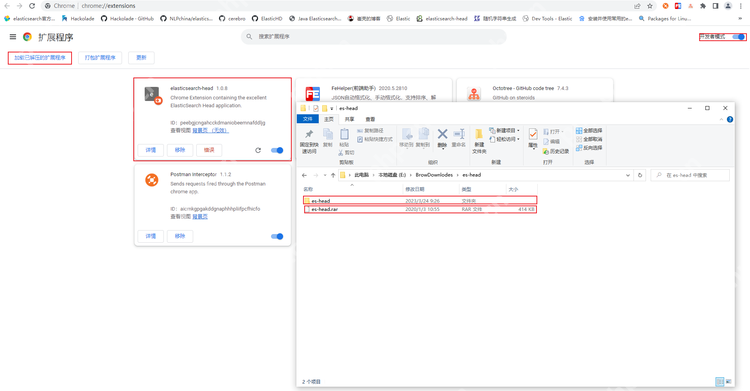
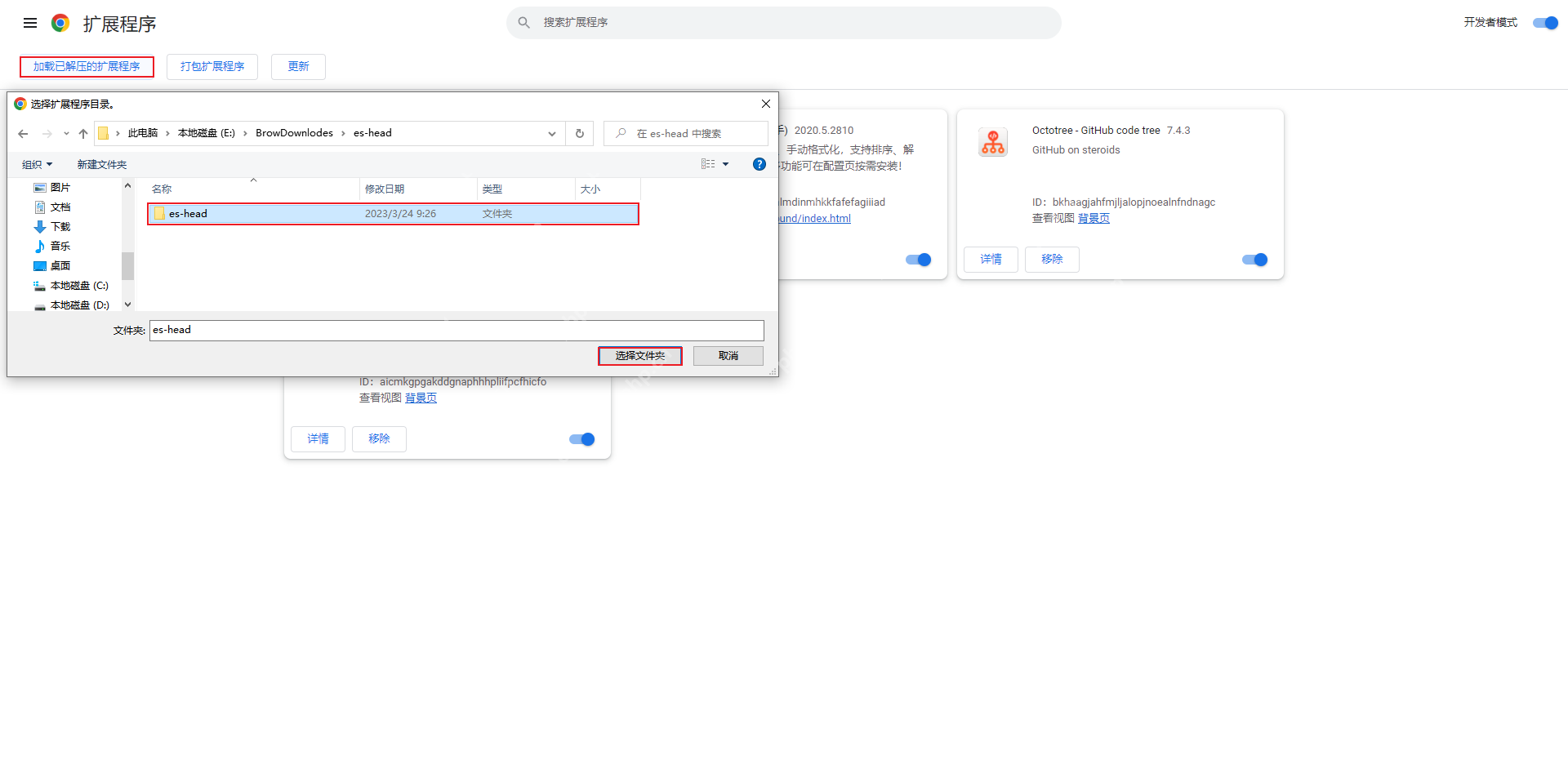
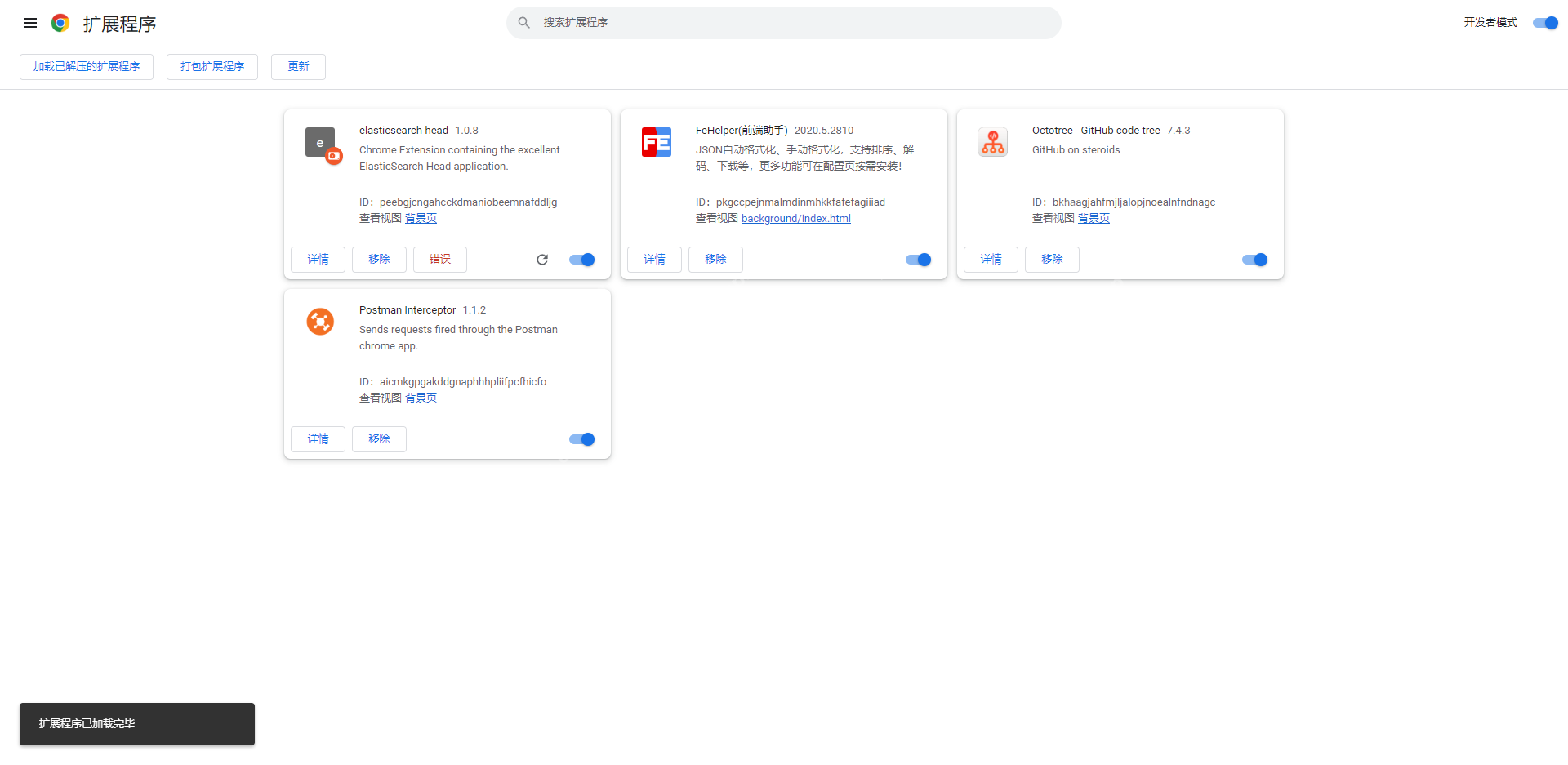
At this point, the elasticsearch-head plug-in is installed.
Method 2: Install through Chrome Group Policy Management Template
First, download the [Chrome Group Policy Management Template] and unzip it, and find the "chrome.adm" file in the [policy_templates\windows\adm\zh-CN] folder.
Chrome Group Policy Management Template Download Link: http://m.miracleart.cn/link/b0ea65d0755634f5b2400f9925ad392b
Press [Win R] to open and run, enter [gpedit.msc] to enter the local Group Policy Editor. Expand [Local Computer Policy > Computer Configuration > Administrative Templates], right-click on "Administrative Templates", and select "Add/Remove Templates".
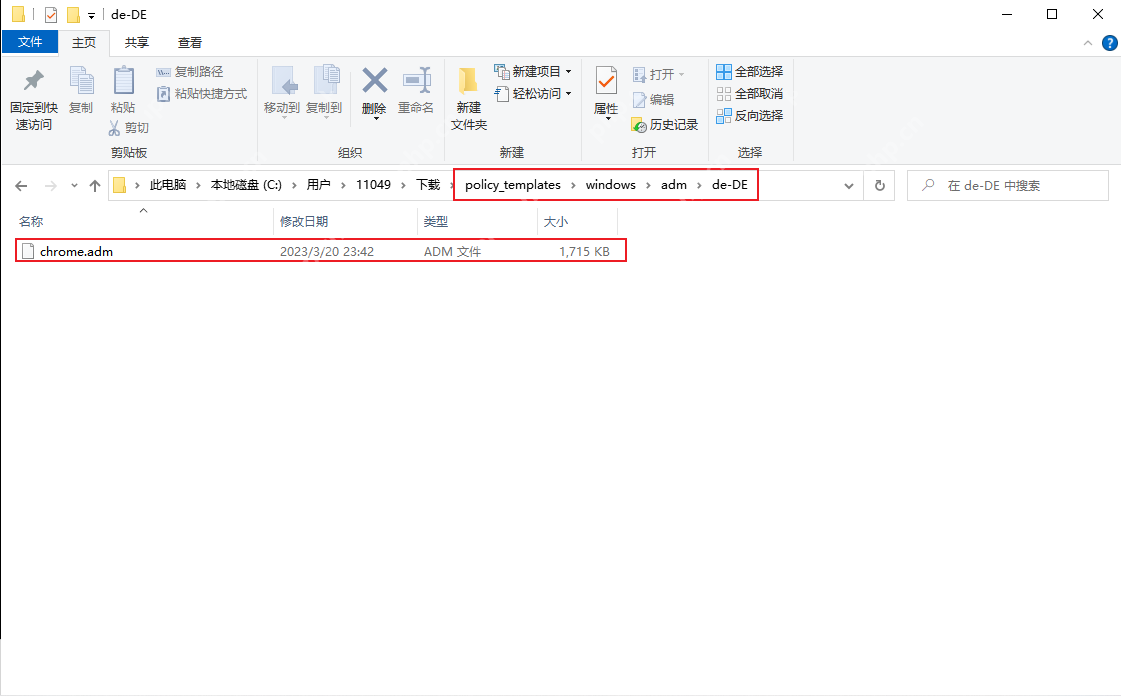
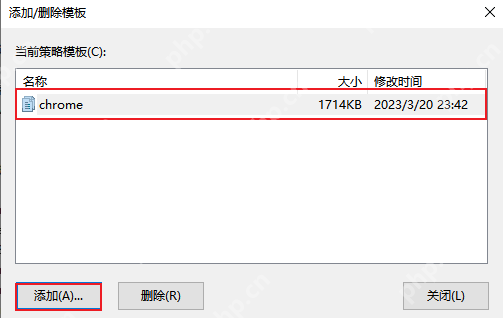
Click [Add], select the "chrome.adm" file to open, and then close the "Add/Remove Template" window.
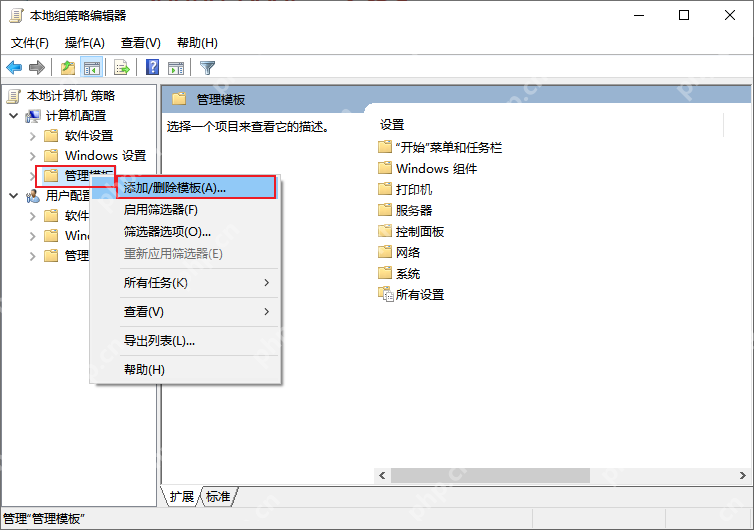
After the Chrome.adm configuration plug-in is installed, you can find configuration items for various Chrome functions in [Local Computer Policy > Computer Configuration > Administrative Templates > Classic Administrative Templates (ADM) > Google -> Google Chrome].
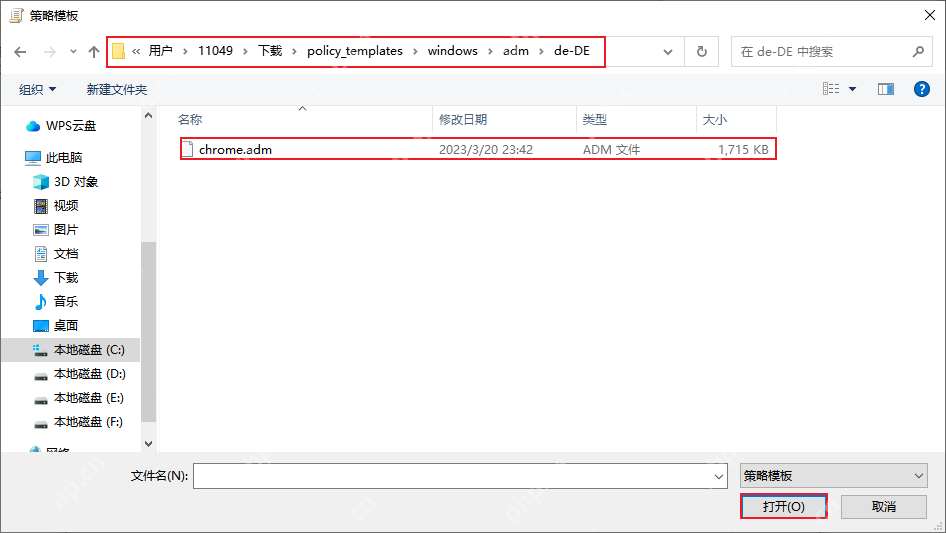
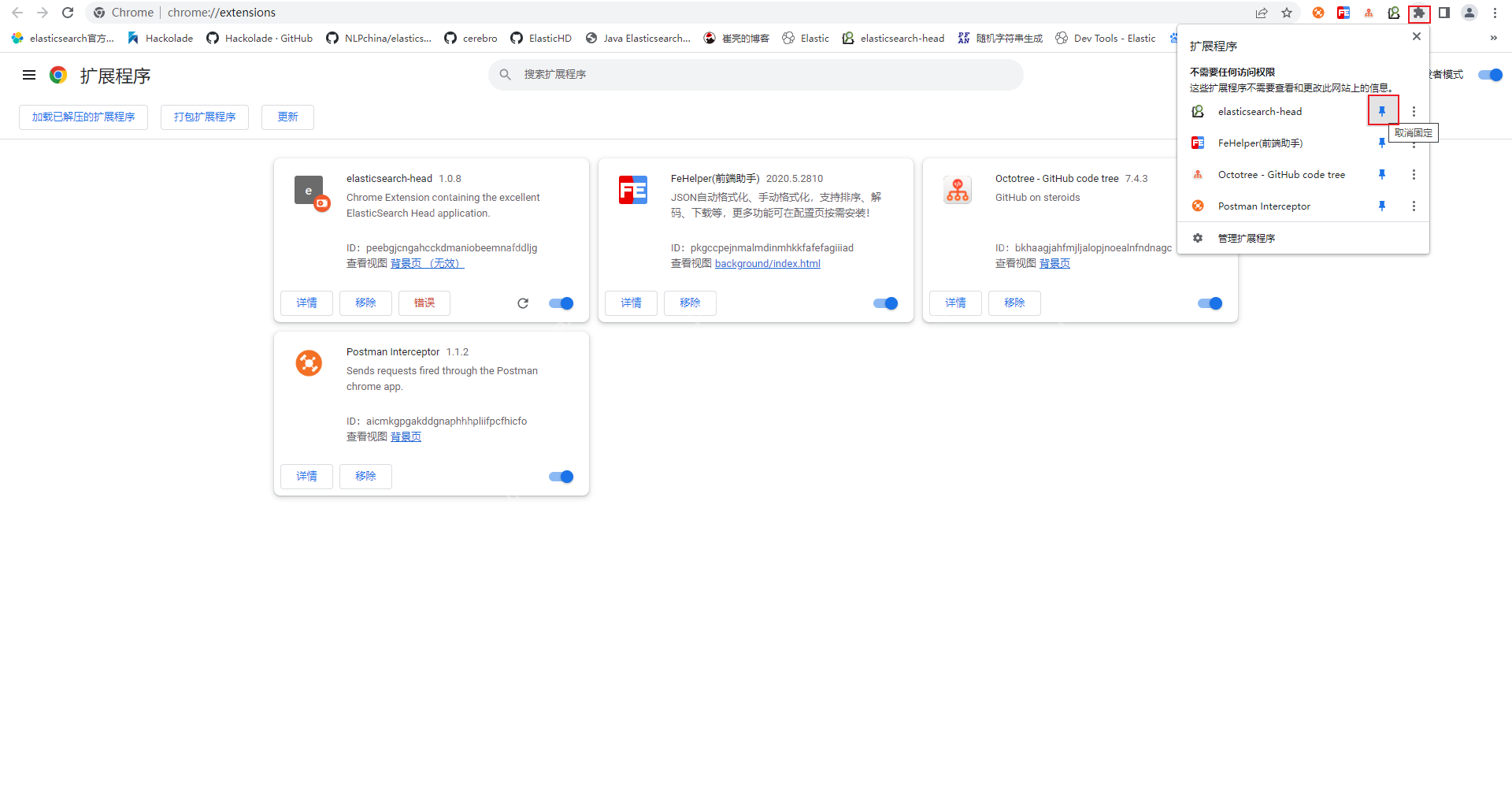
After the import is successful, open [Classic Administrative Templates], click [Google], and then click [Configure the list of forced installation extensions] to copy the extension ID in Google Chrome and add it to this configuration (ID: the ID in the first step).
Erweiterungen -> Liste der Apps und Erweiterungen konfigurieren, deren Installation erzwungen wurde
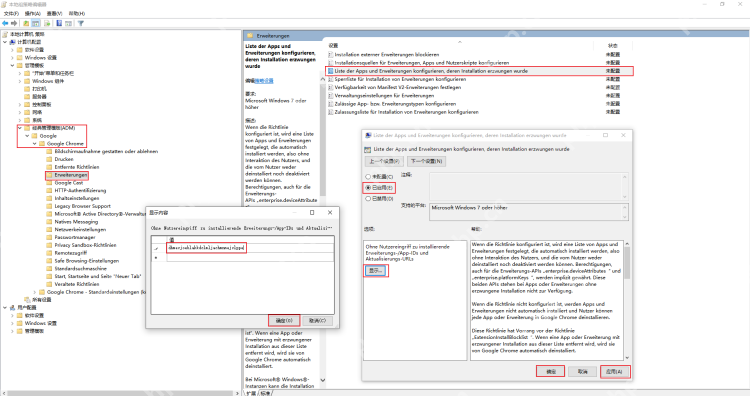
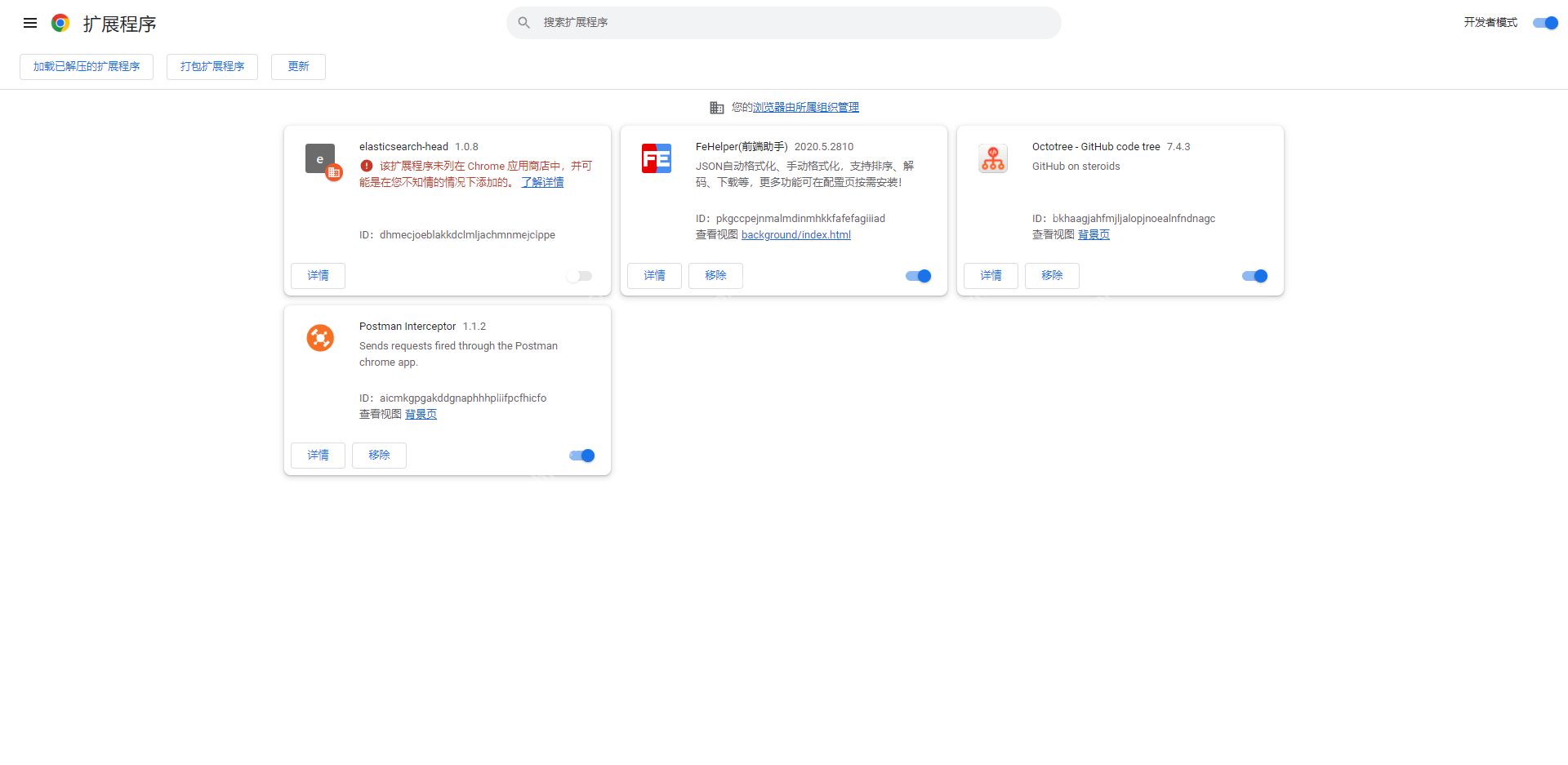
After the operation is completed, go back to the chrome extension list page and you can see the disabled extension. The enable option on the right has become a checkable state. Just check to enable the extension.
Explanation of terms
- Bildschirmaufnahme gestatten oder ablehnen - Allow or deny screen capture
- Drucken - Print
- Entfernte Richtlinien - Remote Commands
- Erweiterungen - Extensions
- Google Cast - Google Play
- HTTP-Authentifizierung - HTTP Authentication
- Inhaltseinstellungen - Content Settings
- Legacy Browser Support - Legacy Browser Support
- Microsoft? Active Directory?-Verwaltungseinstellungen - Microsoft Active Directory? Management Settings
- Natives Messaging - Native Messaging
- Netzwerkeinstellungen - Network Settings
- Passwortmanager - Password Manager
- Privacy Sandbox-Richtlinien - Privacy Sandbox Policy
- Remotezugriff - Remote access
- Safe Browsing-Einstellungen - Safe Browsing Settings
- Standardsuchmaschine - Default search engine
- Start, Startseite und Seite "Neuer Tab" - Home, Home and Page "New Tab"
- Veraltete Richtlinien - Obsolete Commands
- Installation external Erweiterungen blockieren - Block installation of external extensions
- Installationsquellen für Erweiterungen, Apps und Nutzerskripte konfigurieren - Installation source for configuration extensions, applications and user scripts
- Liste der Apps und Erweiterungen konfigurieren, deren Installation erzwungen wurde - Configure a list of forced installation applications and extensions
- Sperrliste für Installation von Erweiterungen konfigurieren - Configure blacklists for installing extensions
- Verfügbarkeit von Manifest?V2-Erweiterungen festlegen - Availability of the declaration? Set up V2 extensions
- Verwaltungseinstellungen für Erweiterungen - Extended management settings
- Zul?ssige App- bzw. Erweiterungstypen konfigurieren - Zul? Application or application. Configure extension type
- Zulassungsliste für Installation von Erweiterungen konfigurieren - Configure the approval list for installing extensions
The above is the detailed content of 【ES 3rd Anniversary】Windows-chrome installation of Elasticsearch-head plug-in. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undress AI Tool
Undress images for free

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 The role of Ethereum smart contracts
Jul 15, 2025 pm 09:18 PM
The role of Ethereum smart contracts
Jul 15, 2025 pm 09:18 PM
The role of Ethereum smart contract is to realize decentralized, automated and transparent protocol execution. Its core functions include: 1. As the core logic layer of DApp, it supports token issuance, DeFi, NFT and other functions; 2. Automatically execute contracts through code to reduce the risks of human intervention and fraud; 3. Build a DeFi ecosystem so that users can directly conduct financial operations such as lending and transactions; 4. Create and manage digital assets to ensure uniqueness and verifiability; 5. Improve the transparency and security of supply chain and identity verification; 6. Support DAO governance and realize decentralized decision-making.
 How to identify fake altcoins? Teach you to avoid cryptocurrency fraud
Jul 15, 2025 pm 10:36 PM
How to identify fake altcoins? Teach you to avoid cryptocurrency fraud
Jul 15, 2025 pm 10:36 PM
To identify fake altcoins, you need to start from six aspects. 1. Check and verify the background of the materials and project, including white papers, official websites, code open source addresses and team transparency; 2. Observe the online platform and give priority to mainstream exchanges; 3. Beware of high returns and people-pulling modes to avoid fund traps; 4. Analyze the contract code and token mechanism to check whether there are malicious functions; 5. Review community and media operations to identify false popularity; 6. Follow practical anti-fraud suggestions, such as not believing in recommendations or using professional wallets. The above steps can effectively avoid scams and protect asset security.
 How much is a stablecoin USD
Jul 15, 2025 pm 09:57 PM
How much is a stablecoin USD
Jul 15, 2025 pm 09:57 PM
The value of stablecoins is usually pegged to the US dollar 1:1, but it will fluctuate slightly due to factors such as market supply and demand, investor confidence and reserve assets. For example, USDT fell to $0.87 in 2018, and USDC fell to around $0.87 in 2023 due to the Silicon Valley banking crisis. The anchoring mechanism of stablecoins mainly includes: 1. fiat currency reserve type (such as USDT, USDC), which relies on the issuer's reserves; 2. cryptocurrency mortgage type (such as DAI), which maintains stability by over-collateralizing other cryptocurrencies; 3. Algorithmic stablecoins (such as UST), which relies on algorithms to adjust supply, but have higher risks. Common trading platforms recommendations include: 1. Binance, providing rich trading products and strong liquidity; 2. OKX,
 Which is better, DAI or USDC?_Is DAI suitable for long-term holding?
Jul 15, 2025 pm 11:18 PM
Which is better, DAI or USDC?_Is DAI suitable for long-term holding?
Jul 15, 2025 pm 11:18 PM
Is DAI suitable for long-term holding? The answer depends on individual needs and risk preferences. 1. DAI is a decentralized stablecoin, generated by excessive collateral for crypto assets, suitable for users who pursue censorship resistance and transparency; 2. Its stability is slightly inferior to USDC, and may experience slight deansal due to collateral fluctuations; 3. Applicable to lending, pledge and governance scenarios in the DeFi ecosystem; 4. Pay attention to the upgrade and governance risks of MakerDAO system. If you pursue high stability and compliance guarantees, it is recommended to choose USDC; if you attach importance to the concept of decentralization and actively participate in DeFi applications, DAI has long-term value. The combination of the two can also improve the security and flexibility of asset allocation.
 Is USDT worth investing in stablecoin_Is USDT a good investment project?
Jul 15, 2025 pm 11:45 PM
Is USDT worth investing in stablecoin_Is USDT a good investment project?
Jul 15, 2025 pm 11:45 PM
USDT is not suitable as a traditional value-added asset investment, but can be used as an instrumental asset to participate in financial management. 1. The USDT price is anchored to the US dollar and does not have room for appreciation. It is mainly suitable for trading, payment and risk aversion; 2. Suitable for risk aversion investors, arbitrage traders and investors waiting for entry opportunities; 3. Stable returns can be obtained through DeFi pledge, CeFi currency deposit, liquidity provision, etc.; 4. Be wary of centralized risks, regulatory changes and counterfeit currency risks; 5. In summary, USDT is a good risk aversion and transitional asset. If you pursue stable returns, it should be combined with its use in financial management scenarios, rather than expecting its own appreciation.
 Is USDC safe? What is the difference between USDC and USDT
Jul 15, 2025 pm 11:48 PM
Is USDC safe? What is the difference between USDC and USDT
Jul 15, 2025 pm 11:48 PM
USDC is safe. It is jointly issued by Circle and Coinbase. It is regulated by the US FinCEN. Its reserve assets are US dollar cash and US bonds. It is regularly audited independently, with high transparency. 1. USDC has strong compliance and is strictly regulated by the United States; 2. The reserve asset structure is clear, supported by cash and Treasury bonds; 3. The audit frequency is high and transparent; 4. It is widely accepted by institutions in many countries and is suitable for scenarios such as DeFi and compliant payments. In comparison, USDT is issued by Tether, with an offshore registration location, insufficient early disclosure, and reserves with low liquidity assets such as commercial paper. Although the circulation volume is large, the regulatory recognition is slightly low, and it is suitable for users who pay attention to liquidity. Both have their own advantages, and the choice should be determined based on the purpose and preferences of use.
 LayerZero, StarkNet, ZK Ecological Preheat: How long can the airdrop bonus last?
Jul 16, 2025 am 10:06 AM
LayerZero, StarkNet, ZK Ecological Preheat: How long can the airdrop bonus last?
Jul 16, 2025 am 10:06 AM
The duration of the airdrop dividend is uncertain, but the LayerZero, StarkNet and ZK ecosystems still have long-term value. 1. LayerZero achieves cross-chain interoperability through lightweight protocols; 2. StarkNet provides efficient and low-cost Ethereum L2 expansion solutions based on ZK-STARKs technology; 3. ZK ecosystem (such as zkSync, Scroll, etc.) expands the application of zero-knowledge proof in scaling and privacy protection; 4. Participation methods include the use of bridging tools, interactive DApps, participating test networks, pledged assets, etc., aiming to experience the next generation of blockchain infrastructure in advance and strive for potential airdrop opportunities.
 How to calculate the altcoin transfer fee? Analysis of cost differences between different chains
Jul 15, 2025 pm 10:54 PM
How to calculate the altcoin transfer fee? Analysis of cost differences between different chains
Jul 15, 2025 pm 10:54 PM
The altcoin transfer fee varies from chain to chain and is mainly determined by the basic network fee, transaction speed and Gas unit. 1. The Ethereum fee is high, with an average of US$2~20 per transaction, suitable for high-value transactions; 2. The Binance Smart Chain fee is low, about US$0.1~0.3, suitable for daily operations; 3. The Solana fee is extremely low, usually below US$0.0001, suitable for high-frequency transactions; 4. The Polygon fee is less than US$0.01, compatible with EVM; 5. TRON focuses on low-cost, and the handling fee is almost negligible. Users should reasonably choose the transfer method based on the characteristics of the chain, network congestion and gas fluctuations, and at the same time confirm that the token belongs to the same link as the receiver to avoid asset losses.





