 Backend Development
Backend Development
 C#.Net Tutorial
C#.Net Tutorial
 Share the MD5 algorithm example code based on string encryption
Share the MD5 algorithm example code based on string encryption
Share the MD5 algorithm example code based on string encryption
Jul 26, 2017 pm 03:01 PMMD5 algorithm based on string encryption, VS2008 VC++, multi-byte compilation project. The main code is as follows, which implements ANSI string encryption and Unicode string encryption.
The running effect is as follows:
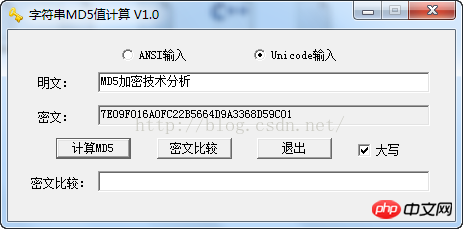
Core code:
void CEncryptByMd5Dlg::OnButtonOk()
{
// TODO: Add your control notification handler code here
UpdateData(true);
unsigned int len=0;
char *cTemp =NULL;
if(m_bType==0)
{
len=m_sText.GetLength();
cTemp=(char*)(LPCTSTR)m_sText;
}
else
{
len=CStringW(m_sText).GetLength()*2;
cTemp=(char*)ANSI2UNICODE(m_sText);
}
char *cIdentity;
CMd5A md5;
cIdentity = md5.MDString(cTemp,len);
m_sEncrypt = CString(cIdentity);
if(m_bUpper==TRUE)
{
m_sEncrypt.MakeUpper();
}
else
{
m_sEncrypt.MakeLower();
}
UpdateData(false);
}
void CEncryptByMd5Dlg::OnBnClickedBtnCompare()
{
// TODO: Add your control notification handler code here
UpdateData(true);
if(m_sEncrypt==m_szMD5_2)
{
MessageBox(_T("密文比較結(jié)果相同!"),_T("比較相同"),MB_OK|MB_ICONINFORMATION);
}
else
{
MessageBox(_T("密文比較結(jié)果失?。?quot;),_T("比較不同"),MB_OK|MB_ICONERROR);
}
UpdateData(FALSE);
}
void CEncryptByMd5Dlg::OnEnChangeEdit1()
{
// TODO: If this is a RICHEDIT control, the control will not
// send this notification unless you override the CDialog::OnInitDialog()
// function and call CRichEditCtrl().SetEventMask()
// with the ENM_CHANGE flag ORed into the mask.
OnButtonOk();
// TODO: Add your control notification handler code here
}
char * CEncryptByMd5Dlg::Unicode2ANSI(CString strSource)
{
if (strSource.IsEmpty()) return NULL;
char *pBuffer = NULL;
int nBufferSize = 0;
#ifdef _UNICODE
nBufferSize = WideCharToMultiByte(CP_ACP, 0, (LPCTSTR)strSource, -1, NULL, 0, NULL, NULL) + 1;
pBuffer = new char[nBufferSize];
memset(pBuffer, 0, sizeof(char)*nBufferSize);
WideCharToMultiByte(CP_ACP, 0, (LPCTSTR)strSource, -1, pBuffer, nBufferSize, NULL, NULL);
#else
nBufferSize = strSource.GetLength() + 1;
pBuffer = new char[nBufferSize];
memset(pBuffer, 0, sizeof(char)*nBufferSize);
strcpy_s(pBuffer, nBufferSize, (LPCTSTR)strSource);
#endif
return pBuffer;
}
wchar_t * CEncryptByMd5Dlg::ANSI2UNICODE(CString pData)
{
int nLength = MultiByteToWideChar(CP_ACP, 0, pData, -1, NULL, 0);
wchar_t *pwBuffer = new wchar_t[nLength + 1];
memset(pwBuffer, 0, sizeof(wchar_t)*(nLength + 1));
MultiByteToWideChar(CP_ACP, 0, pData, -1, pwBuffer, nLength);
return pwBuffer;
}
void CEncryptByMd5Dlg::OnBnClickedCheckUpper()
{
OnButtonOk();
// TODO: Add your control notification handler code here
}
void CEncryptByMd5Dlg::OnBnClickedRadio1()
{
OnButtonOk();
// TODO: Add your control notification handler code here
}
void CEncryptByMd5Dlg::OnBnClickedRadio2()
{
OnButtonOk();
// TODO: Add your control notification handler code here
}The above is the detailed content of Share the MD5 algorithm example code based on string encryption. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undress AI Tool
Undress images for free

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 Implementing Machine Learning Algorithms in C++: Common Challenges and Solutions
Jun 03, 2024 pm 01:25 PM
Implementing Machine Learning Algorithms in C++: Common Challenges and Solutions
Jun 03, 2024 pm 01:25 PM
Common challenges faced by machine learning algorithms in C++ include memory management, multi-threading, performance optimization, and maintainability. Solutions include using smart pointers, modern threading libraries, SIMD instructions and third-party libraries, as well as following coding style guidelines and using automation tools. Practical cases show how to use the Eigen library to implement linear regression algorithms, effectively manage memory and use high-performance matrix operations.
 Application of algorithms in the construction of 58 portrait platform
May 09, 2024 am 09:01 AM
Application of algorithms in the construction of 58 portrait platform
May 09, 2024 am 09:01 AM
1. Background of the Construction of 58 Portraits Platform First of all, I would like to share with you the background of the construction of the 58 Portrait Platform. 1. The traditional thinking of the traditional profiling platform is no longer enough. Building a user profiling platform relies on data warehouse modeling capabilities to integrate data from multiple business lines to build accurate user portraits; it also requires data mining to understand user behavior, interests and needs, and provide algorithms. side capabilities; finally, it also needs to have data platform capabilities to efficiently store, query and share user profile data and provide profile services. The main difference between a self-built business profiling platform and a middle-office profiling platform is that the self-built profiling platform serves a single business line and can be customized on demand; the mid-office platform serves multiple business lines, has complex modeling, and provides more general capabilities. 2.58 User portraits of the background of Zhongtai portrait construction
 Improved detection algorithm: for target detection in high-resolution optical remote sensing images
Jun 06, 2024 pm 12:33 PM
Improved detection algorithm: for target detection in high-resolution optical remote sensing images
Jun 06, 2024 pm 12:33 PM
01 Outlook Summary Currently, it is difficult to achieve an appropriate balance between detection efficiency and detection results. We have developed an enhanced YOLOv5 algorithm for target detection in high-resolution optical remote sensing images, using multi-layer feature pyramids, multi-detection head strategies and hybrid attention modules to improve the effect of the target detection network in optical remote sensing images. According to the SIMD data set, the mAP of the new algorithm is 2.2% better than YOLOv5 and 8.48% better than YOLOX, achieving a better balance between detection results and speed. 02 Background & Motivation With the rapid development of remote sensing technology, high-resolution optical remote sensing images have been used to describe many objects on the earth’s surface, including aircraft, cars, buildings, etc. Object detection in the interpretation of remote sensing images
 Groundbreaking CVM algorithm solves more than 40 years of counting problems! Computer scientist flips coin to figure out unique word for 'Hamlet'
Jun 07, 2024 pm 03:44 PM
Groundbreaking CVM algorithm solves more than 40 years of counting problems! Computer scientist flips coin to figure out unique word for 'Hamlet'
Jun 07, 2024 pm 03:44 PM
Counting sounds simple, but in practice it is very difficult. Imagine you are transported to a pristine rainforest to conduct a wildlife census. Whenever you see an animal, take a photo. Digital cameras only record the total number of animals tracked, but you are interested in the number of unique animals, but there is no statistics. So what's the best way to access this unique animal population? At this point, you must be saying, start counting now and finally compare each new species from the photo to the list. However, this common counting method is sometimes not suitable for information amounts up to billions of entries. Computer scientists from the Indian Statistical Institute, UNL, and the National University of Singapore have proposed a new algorithm - CVM. It can approximate the calculation of different items in a long list.
 User profiling algorithms: history, current situation and future
Apr 11, 2024 pm 01:40 PM
User profiling algorithms: history, current situation and future
Apr 11, 2024 pm 01:40 PM
1. Introduction to user portraits A portrait is a structured description of a user that is understandable by humans and readable and writeable by machines. It not only provides personalized services, but also plays an important role in the company's strategic decision-making and business analysis. 1. The classification of portraits is divided into social general knowledge and domain knowledge based on data sources. General social portraits can be divided into static and dynamic categories according to the time dimension. The most common static general social portraits include demographic characteristics, such as gender, household registration, graduation school, etc. These contents are displayed over a relatively long period of time. The windows are relatively static. In addition to using it in pictures, it is also often used in demography, demography, sociology, etc. Dynamic social general portraits are more important, also known as life stage portraits. For example, in e-commerce, people
 Which of the top ten virtual currency trading apps is the best? Which of the top ten virtual currency trading apps is the most reliable
Mar 19, 2025 pm 05:00 PM
Which of the top ten virtual currency trading apps is the best? Which of the top ten virtual currency trading apps is the most reliable
Mar 19, 2025 pm 05:00 PM
Top 10 virtual currency trading apps rankings: 1. OKX, 2. Binance, 3. Gate.io, 4. Kraken, 5. Huobi, 6. Coinbase, 7. KuCoin, 8. Crypto.com, 9. Bitfinex, 10. Gemini. Security, liquidity, handling fees, currency selection, user interface and customer support should be considered when choosing a platform.
 Get the gate.io installation package for free
Feb 21, 2025 pm 08:21 PM
Get the gate.io installation package for free
Feb 21, 2025 pm 08:21 PM
Gate.io is a popular cryptocurrency exchange that users can use by downloading its installation package and installing it on their devices. The steps to obtain the installation package are as follows: Visit the official website of Gate.io, click "Download", select the corresponding operating system (Windows, Mac or Linux), and download the installation package to your computer. It is recommended to temporarily disable antivirus software or firewall during installation to ensure smooth installation. After completion, the user needs to create a Gate.io account to start using it.
 Focus on it! ! Analysis of two major algorithm frameworks for causal inference
Jun 04, 2024 pm 04:45 PM
Focus on it! ! Analysis of two major algorithm frameworks for causal inference
Jun 04, 2024 pm 04:45 PM
1. The main tasks of the overall framework can be divided into three categories. The first is the discovery of causal structures, that is, identifying causal relationships between variables from the data. The second is the estimation of causal effects, that is, inferring from the data the degree of influence of one variable on another variable. It should be noted that this impact does not refer to relative nature, but to how the value or distribution of another variable changes when one variable is intervened. The last step is to correct for bias, because in many tasks, various factors may cause the distribution of development samples and application samples to be different. In this case, causal inference may help us correct for bias. These functions are suitable for a variety of scenarios, the most typical of which is decision-making scenarios. Through causal inference, we can understand how different users react to our decision-making behavior. Secondly, in industry





