Model Context Protocol (MCP): A Security Minefield for AI Agents
Often dubbed the "USB-C for AI agents," the Model Context Protocol (MCP) is the standard for connecting large language models (LLMs) with external tools and data. This allows AI agents to interact seamlessly with various services, execute commands, and share context. However, MCP's inherent insecurity poses significant risks. Connecting your AI agent to untrusted MCP servers could inadvertently expose your system to malicious attacks, compromising shell access, secrets, or even your entire infrastructure. This article details these security vulnerabilities, their potential impact, and mitigation strategies.

Key Security Risks and Mitigation:
Recent research from Leidos highlights critical vulnerabilities within MCP, demonstrating how attackers can exploit LLMs like Claude and Llama to execute malicious code, gain unauthorized access, and steal credentials. The researchers also developed a tool to identify and address these vulnerabilities.

-
Command Injection: Manipulating prompts can trick AI agents into executing harmful commands if user input is directly processed into shell commands or SQL queries. This mirrors traditional injection attacks but is amplified by the dynamic nature of prompt processing.
- Mitigation: Implement rigorous input sanitization, parameterized queries, and strict execution boundaries.

-
Tool Poisoning: Malicious tools can contain deceptive documentation or hidden code that alters agent behavior. LLMs, trusting tool descriptions implicitly, can be manipulated into revealing private keys or leaking files.
- Mitigation: Thoroughly verify tool sources, ensure full metadata transparency, and sandbox tool execution.

-
Server-Sent Events (SSE) Vulnerabilities: The persistent connections used by SSE for live data streams create attack vectors. Hijacked streams or timing glitches can lead to data injection, replay attacks, or session bleed.
- Mitigation: Enforce HTTPS, validate connection origins, and implement strict timeouts.

-
Privilege Escalation: A compromised tool can impersonate others, potentially gaining unauthorized access. For instance, a fake plugin might mimic a Slack integration, leading to message leaks.
- Mitigation: Isolate tool permissions, rigorously validate tool identities, and enforce authentication for all inter-tool communication.

-
Persistent Context: MCP sessions often retain previous inputs and outputs, creating risks if sensitive information is reused across sessions or if attackers manipulate the context over time.
- Mitigation: Implement regular session data clearing, limit context retention, and isolate user sessions.

-
Server Data Takeover: A compromised tool can trigger a cascading effect, allowing a malicious server to access data from other connected systems (e.g., WhatsApp, Notion, AWS).
- Mitigation: Adopt a zero-trust architecture, use scoped tokens, and establish emergency revocation protocols.

Risk Summary Table: (Similar to the original table but slightly reformatted for clarity)
| Vulnerability | Severity | Attack Vector | Impact Level | Recommended Mitigation |
|---|---|---|---|---|
| Command Injection | Moderate | Malicious prompt input to shell/SQL tools | Remote Code Execution, Data Leak | Input sanitization, parameterized queries, strict command guards |
| Tool Poisoning | Severe | Malicious docstrings or hidden tool logic | Secret Leaks, Unauthorized Actions | Vet tool sources, expose full metadata, sandbox tool execution |
| Server-Sent Events | Moderate | Persistent open connections (SSE/WebSocket) | Session Hijack, Data Injection | Use HTTPS, enforce timeouts, validate origins |
| Privilege Escalation | Severe | One tool impersonating or misusing another | Unauthorized Access, System Abuse | Isolate scopes, verify tool identity, restrict cross-tool communication |
| Persistent Context | Low/Mod | Stale session data or poisoned memory | Info Leakage, Behavioral Drift | Clear session data regularly, limit context lifetime, isolate user sessions |
| Server Data Takeover | Severe | One compromised server pivoting across tools | Multi-system Breach, Credential Theft | Zero-trust setup, scoped tokens, kill-switch on compromise |
Conclusion:
MCP, while facilitating powerful LLM integrations, presents significant security challenges. As AI agents become more sophisticated, these vulnerabilities will only increase in severity. Developers must prioritize secure defaults, conduct thorough tool audits, and treat MCP servers with the same caution as any third-party code. Promoting secure protocols is crucial for building a safer infrastructure for future MCP integrations.
Frequently Asked Questions (FAQs): (Similar to the original FAQs but rephrased for better flow)
-
Q1: What is MCP, and why is its security important? A1: MCP is the connection point for AI agents to access tools and services. Without proper security, it's an open door for attackers.
-
Q2: How can AI agents be tricked into executing harmful commands? A2: If user input isn't sanitized before being used in shell commands or SQL queries, it can lead to remote code execution.
-
Q3: What is the significance of "tool poisoning"? A3: Malicious tools can embed hidden instructions in their descriptions, which the LLM might blindly execute. Thorough vetting and sandboxing are essential.
-
Q4: Can one tool compromise others within MCP? A4: Yes, this is privilege escalation. A compromised tool can impersonate or misuse others unless permissions and identities are strictly controlled.
-
Q5: What's the worst-case scenario if these risks are ignored? A5: A single compromised server could lead to a complete system breach, including credential theft, data leaks, and total system compromise.
? ??? 6 MCP? ?? ?? : ?? ??? ?? - ?? Vidhya? ?? ?????. ??? ??? PHP ??? ????? ?? ?? ??? ?????!

? AI ??

Undress AI Tool
??? ???? ??

Undresser.AI Undress
???? ?? ??? ??? ?? AI ?? ?

AI Clothes Remover
???? ?? ???? ??? AI ?????.

Clothoff.io
AI ? ???

Video Face Swap
??? ??? AI ?? ?? ??? ???? ?? ???? ??? ?? ????!

?? ??

??? ??

???++7.3.1
???? ?? ?? ?? ???

SublimeText3 ??? ??
??? ??, ???? ?? ????.

???? 13.0.1 ???
??? PHP ?? ?? ??

???? CS6
??? ? ?? ??

SublimeText3 Mac ??
? ??? ?? ?? ?????(SublimeText3)
 Kimi K2 : ?? ??? ?? ?? ???? ??
Jul 12, 2025 am 09:16 AM
Kimi K2 : ?? ??? ?? ?? ???? ??
Jul 12, 2025 am 09:16 AM
?? ? Genai ??? ?? ? ?? ?? ?? ??? ??? ??????? DeepSeek? ???? ?? ??? ?? ??? Kimi K1.5? ???? ???? ?? ? ??????. ??? ??? ?? ??????.
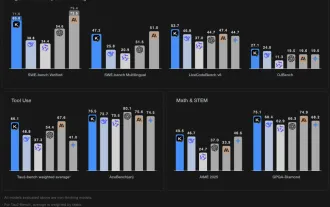
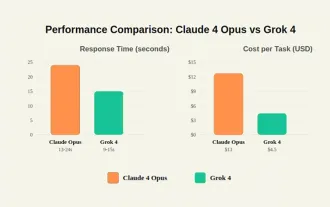 Grok 4 vs Claude 4 : ?? ?? ? ?????
Jul 12, 2025 am 09:37 AM
Grok 4 vs Claude 4 : ?? ?? ? ?????
Jul 12, 2025 am 09:37 AM
20125 ? ???? AI“?? ??”? ???? ??? Xai? Anthropic? ???? ?? ? Grok 4? Claude 4? ??????.? ? ??? ??? ??? ?? ???? ??? ?? ????.
 ??? ?? ??? ?? ?? ??? ??? ?? 10 ?
Jul 16, 2025 am 11:12 AM
??? ?? ??? ?? ?? ??? ??? ?? 10 ?
Jul 16, 2025 am 11:12 AM
??? ??? ??? 10 ?? ??? ??? ?? ????. ???, ???? ???? ??? ?? ??? ? ?? ??? ?? ? ??? ?? ?? ??? ????. ?? ? ? ?? ?? ??? ??? ?? ??? T?? ??? ?? ?????.
 ???? ?????? ' New ' ???? ?????
Jul 12, 2025 am 09:33 AM
???? ?????? ' New ' ???? ?????
Jul 12, 2025 am 09:33 AM
?? ?? ???? ?????? ?? ?? ?? (LLM)? ?? ???? ? ??? ??? ???????. ??? ??? LLM? ??? ???? ?? ??????. ??? ??? ??
 Leia 's Inmersity Mobile ?? ?? ??? 3D ??? ?????.
Jul 09, 2025 am 11:17 AM
Leia 's Inmersity Mobile ?? ?? ??? 3D ??? ?????.
Jul 09, 2025 am 11:17 AM
Leia? ??? ?? ?? ??? ???? ?? ??? ?????? ???? ?, ? ? ?? ??? ?? ????? ? ??? ?? ???? ??? ???? SCE? ????? ????? ?? ??? ?? ????.
 AI ????? 7 ?? ??? ??????
Jul 11, 2025 am 11:08 AM
AI ????? 7 ?? ??? ??????
Jul 11, 2025 am 11:08 AM
???? ??? ?? ???? ?? ??? ???? ?? ? ??? ? AI ??? ?? ??? ?? ????? ? ?? ??????? ?? ?? ?? ?? ?? ?? ??? ???? ??? ???.
 ? AI ??? ??? ??? ???? ??? ?????
Jul 09, 2025 am 11:16 AM
? AI ??? ??? ??? ???? ??? ?????
Jul 09, 2025 am 11:16 AM
King 's College London? University of Oxford? ????? ??? ??? ??? Openai, Google ? Anthropic? ?? ? ??? ???? ???? ? ?? ???? ?? ???? ?? ??? ?????. ??? ????
 ?? ? ?? ?? : ??? ?? AI? ?? ? ????
Jul 13, 2025 am 11:08 AM
?? ? ?? ?? : ??? ?? AI? ?? ? ????
Jul 13, 2025 am 11:08 AM
????? ???? ???? ?????? ??? ??? ??????. 2025 ? 7 ??? ????? ?? ??? ??? ?? ??? ?? ? ??? ??? ??? ??????.? ??? ??? ??????.












