Found a total of 10000 related content

Single Sign-On (SSO) Made Easy
Article Introduction:What is Single Sign-On (SSO)?
Frontend Single Sign-On (SSO) is a user authentication and authorization method enabling users to access multiple applications or websites using a single set of login credentials, eliminating repeated logins and registra
2025-01-21
comment 0
1033

Single Sign-On (SSO) Explained
Article Introduction:Key Takeaways
Single Sign-On (SSO) is a process that allows a user to access multiple services after authenticating their identity only once, which eliminates the need for repeatedly confirming identity through passwords or other systems.
Implem
2025-02-25
comment 0
548

Methods and Implementations of Single Sign-On (SSO)
Article Introduction:An In-Depth Exploration of SSO Techniques
Introduction
Single Sign-On (SSO) is a crucial authentication process that allows users to access multiple applications with one set of login credentials. It streamlines the user experience, enhances secu
2024-11-08
comment 0
1014
Single Sign-On (SSO): A Comprehensive Guide with React and ExpressJS
Article Introduction:Single Sign-On (SSO) is an authentication mechanism that allows users to log in once and access multiple connected applications or systems without needing to reauthenticate for each one. SSO centralizes user authentication into a single, trusted syst
2025-01-06
comment 0
1099

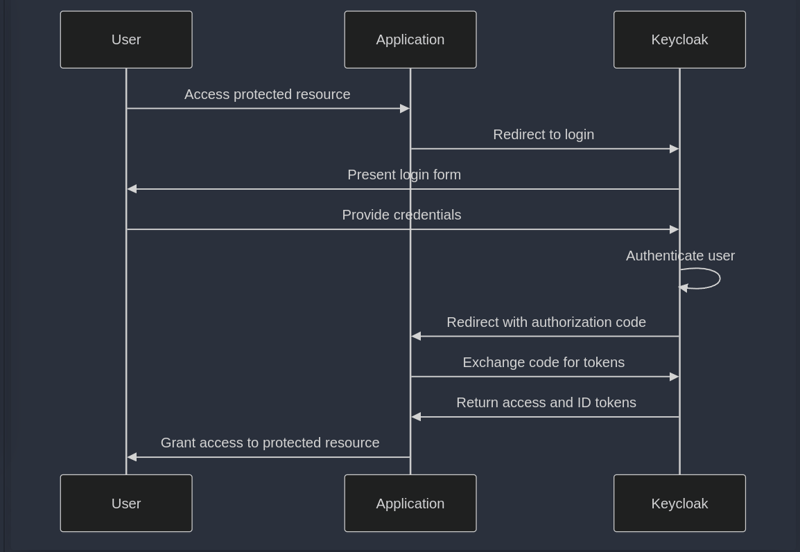


Java Security Frameworks and Libraries (e.g., Keycloak)
Article Introduction:Keycloak is an open source identity and access management solution, suitable for single sign-on and OAuth2/OpenIDConnect authentication and authorization scenarios, suitable for applications that require a unified login system, support multiple clients, and build self-built identity centers. 1. It is out of the box and is simple to configure, suitable for internal enterprise systems or SaaS platforms; 2. Commonly used security libraries in Java such as SpringSecurity, ApacheShiro, and JOSE4J are more inclined to toolkits, suitable for fine-grained permission control or JWT custom processing; 3. In actual use, pay attention to the token validity period and refresh mechanism, cross-domain issues, log audit and dependent version updates to ensure security and system stability.
2025-07-18
comment 0
418


Dave The Diver: How To Catch Spider Crabs
Article Introduction:In Dave The Diver, there are some creatures that are not easy to catch. Or, catch alive that is. The spider crab is one of those very species, making it seem like the only way to bring these crustaceans back up to land is to viciously crack them up w
2025-01-10
comment 0
811

Prepare for Interview Like a Pro with Interview Questions CLI
Article Introduction:Prepare for Interview Like a Pro with Interview Questions CLI
What is the Interview Questions CLI?
The Interview Questions CLI is a command-line tool designed for JavaScript learners and developers who want to enhance their interview
2025-01-10
comment 0
1439

Soft Deletes in Databases: To Use or Not to Use?
Article Introduction:Soft Deletes: A Question of DesignThe topic of soft deletes, a mechanism that "flags" records as deleted instead of physically removing them, has...
2025-01-10
comment 0
1054



















