How to restrict WordPress administrator access through IP address
Apr 20, 2025 am 07:09 AMDo you want to limit access to WordPress admin zones for security reasons?
If you have a small team, a good solution is to limit access to only IP addresses used by team members.
In this article, we will show you how to restrict WordPress administrator access through an IP address.

Why restrict WordPress administrator access through IP addresses?
If you are running a WordPress website, you need to take the security of your website seriously. While WordPress core software is very secure, there are more you can do to protect yourself from hackers.
Hackers can shut down your website and damage your income and reputation. They can steal data, even distribute malware to your website visitors, and blacklist your domain by Google and others.
A wise way to stop hackers is to protect your WordPress admin area from unauthorized access.
If only you or a few trusted users need access to the administrative area, a good way is to restrict access to wp-admin to your team's IP address.
Each team member will connect to your website using a specific IP address for each location. If you block access to all other IP addresses, even if the hacker discovers your username and password, they will not be able to access your website.
Instead, they will see the error message: "Forbidden". You do not have access to this resource. ”
Let's see how to restrict WordPress administrator access through IP addresses.
How to limit WordPress administrator access through IP address
The first thing you need to do is list the IP addresses that everyone needs to log into the WordPress website. If someone works in multiple locations, you will need to collect the IP address for each location.
They can learn about their IP addresses by visiting websites such as SupportAlly.
After you have created your list, you will need to edit the files on the website. You must use the FTP client or hosting provider's file manager application. If you haven't used FTP before, you may want to check out our guide on how to upload files to WordPress using FTP.
You will need to use the software to navigate to your website's /wp-admin/ folder. Once you get there, you should look for that .htaccess file. This is a hidden file, so if you can't see it, you may need to enable the "Show hidden files" option in your software.
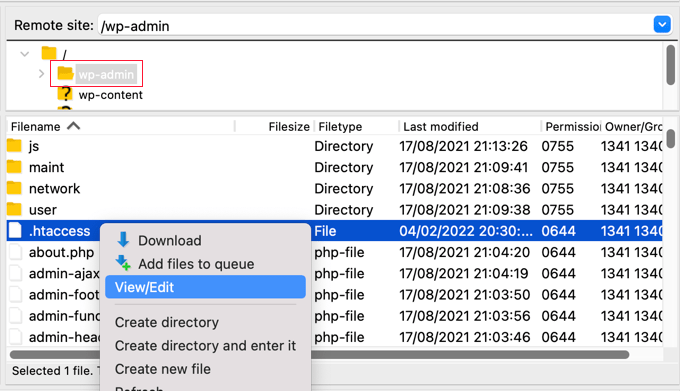
.htaccess If the file does not exist in that folder, you should create a new file and save it with the name in the folder /wp-admin/.
Warning : Do not edit your root .htaccess file, or you will not be able to access the front end of your website! Make sure you are editing /wp-admin/.htaccess.
You should first download a copy of the file to your computer as a backup. Once you have done this you will need to edit the .htaccess and paste the following code:
AuthUserFile /dev/nullAuthGroupFile /dev/nullAuthName "WordPress Admin Access Control"AuthType Basic<limit get>order deny,allowdeny from all# whitelist Syed's IP addressallow from xx.xx.xx.xxx# whitelist David's IP addressallow from xx.xx.xx.xxx# whitelist Amanda's IP addressallow from xx.xx.xx.xxx# whitelist Muhammad's IP addressallow from xx.xx.xx.xxx# whitelist Work IP addressallow from xx.xx.xx.xxx</limit>
Continue editing the file to match the names of your own team members, and paste the IP address you collected earlier to replace the location where it appears xx.xx.xx.xxx.xxx.
After saving the file, only these IP addresses can access the WordPress administrator.
Remember that if your IP address changes or you try to access your website from a new location, you will be locked out of the WordPress admin area. You need to add the new IP address to the file /wp-admin/.htaccess .
We hope this tutorial helps you understand how to limit access to WordPress administrators with IP addresses. You may also want to learn how to get a free SSL certificate for your website, or check out our list of must-have plugins to grow your website.
The above is the detailed content of How to restrict WordPress administrator access through IP address. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undress AI Tool
Undress images for free

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 How to use PHP to build social sharing functions PHP sharing interface integration practice
Jul 25, 2025 pm 08:51 PM
How to use PHP to build social sharing functions PHP sharing interface integration practice
Jul 25, 2025 pm 08:51 PM
The core method of building social sharing functions in PHP is to dynamically generate sharing links that meet the requirements of each platform. 1. First get the current page or specified URL and article information; 2. Use urlencode to encode the parameters; 3. Splice and generate sharing links according to the protocols of each platform; 4. Display links on the front end for users to click and share; 5. Dynamically generate OG tags on the page to optimize sharing content display; 6. Be sure to escape user input to prevent XSS attacks. This method does not require complex authentication, has low maintenance costs, and is suitable for most content sharing needs.
 PHP calls AI intelligent voice assistant PHP voice interaction system construction
Jul 25, 2025 pm 08:45 PM
PHP calls AI intelligent voice assistant PHP voice interaction system construction
Jul 25, 2025 pm 08:45 PM
User voice input is captured and sent to the PHP backend through the MediaRecorder API of the front-end JavaScript; 2. PHP saves the audio as a temporary file and calls STTAPI (such as Google or Baidu voice recognition) to convert it into text; 3. PHP sends the text to an AI service (such as OpenAIGPT) to obtain intelligent reply; 4. PHP then calls TTSAPI (such as Baidu or Google voice synthesis) to convert the reply to a voice file; 5. PHP streams the voice file back to the front-end to play, completing interaction. The entire process is dominated by PHP to ensure seamless connection between all links.
 What is Bitcoin Taproot Upgrade? What are the benefits of Taproot?
Jul 30, 2025 pm 08:27 PM
What is Bitcoin Taproot Upgrade? What are the benefits of Taproot?
Jul 30, 2025 pm 08:27 PM
Directory What is Bitcoin? How does Bitcoin work? Why is Bitcoin not scalable? What is BIP (Bitcoin Improvement Proposal)? What is Bitcoin Taproot Update? Pay to Taproot (P2TR): Benefits of Taproot: Space-saving privacy advantages Security upgrade conclusion: ?Bitcoin is the first digital currency that can send and receive funds without using a third party. Since Bitcoin is software, like any other software, it needs updates and bug fixes. Bitcoin Taproot is such an update that introduces new features to Bitcoin. Cryptocurrency is a hot topic now. People have been talking about it for years, but now with prices rising rapidly, suddenly everyone decides to join and invest in them. Message
 Ethena treasury strategy: the rise of the third empire of stablecoin
Jul 30, 2025 pm 08:12 PM
Ethena treasury strategy: the rise of the third empire of stablecoin
Jul 30, 2025 pm 08:12 PM
The real use of battle royale in the dual currency system has not yet happened. Conclusion In August 2023, the MakerDAO ecological lending protocol Spark gave an annualized return of $DAI8%. Then Sun Chi entered in batches, investing a total of 230,000 $stETH, accounting for more than 15% of Spark's deposits, forcing MakerDAO to make an emergency proposal to lower the interest rate to 5%. MakerDAO's original intention was to "subsidize" the usage rate of $DAI, almost becoming Justin Sun's Solo Yield. July 2025, Ethe
![[2025 Latest] Bitcoin real-time market APP rankings, these 5 are the most accurate and fastest!](https://img.php.cn/upload/article/000/000/083/6888925c6d544409.jpg?x-oss-process=image/resize,m_fill,h_207,w_330) [2025 Latest] Bitcoin real-time market APP rankings, these 5 are the most accurate and fastest!
Jul 29, 2025 pm 05:48 PM
[2025 Latest] Bitcoin real-time market APP rankings, these 5 are the most accurate and fastest!
Jul 29, 2025 pm 05:48 PM
The five most popular Bitcoin market APPs in 2025 are: 1. Binance, whose data comes directly from the world's largest trading pool, updated in milliseconds, suitable for professional traders; 2. Ouyi (OKX), accurate market conditions and smooth APP experience, the first choice for mobile users; 3. Huobi (HTX), a veteran exchange, stable technology, reliable mainstream currency data; 4. Gate.io (Sesame Open Door), rich currency types, is a powerful tool for mining the early market of altcoins; 5. CoinMarketCap, a world-renowned data aggregation platform, integrates data from hundreds of exchanges, provides weighted average reference prices, authoritative and fair.
 Twilio Voice Call Maintenance and Recovery: Detailed Explanation of Meeting Mode and Independent Call Leg Processing
Jul 25, 2025 pm 08:21 PM
Twilio Voice Call Maintenance and Recovery: Detailed Explanation of Meeting Mode and Independent Call Leg Processing
Jul 25, 2025 pm 08:21 PM
This article explores in-depth two main strategies for implementing call hold (Hold) and recovery (Un-hold) in Twilio voice calls. First of all, it is recommended to use the Twilio Conference feature to easily control the retention and recovery of calls by updating the resources of meeting participants, and to configure the retention of music. Second, for more complex independent call leg scenarios, the article explains how to manage call state through carefully designed TwiML streams (such as using, and) to avoid accidental disconnection of non-holding legs and enable call reconnection.
 Why is Bitcoin with a ceiling? Why is the maximum number of Bitcoins 21 million
Jul 30, 2025 pm 10:30 PM
Why is Bitcoin with a ceiling? Why is the maximum number of Bitcoins 21 million
Jul 30, 2025 pm 10:30 PM
The total amount of Bitcoin is 21 million, which is an unchangeable rule determined by algorithm design. 1. Through the proof of work mechanism and the issuance rule of half of every 210,000 blocks, the issuance of new coins decreased exponentially, and the additional issuance was finally stopped around 2140. 2. The total amount of 21 million is derived from summing the equal-scale sequence. The initial reward is 50 bitcoins. After each halving, the sum of the sum converges to 21 million. It is solidified by the code and cannot be tampered with. 3. Since its birth in 2009, all four halving events have significantly driven prices, verified the effectiveness of the scarcity mechanism and formed a global consensus. 4. Fixed total gives Bitcoin anti-inflation and digital yellow metallicity, with its market value exceeding US$2.1 trillion in 2025, becoming the fifth largest capital in the world
 How to buy Bitcoin in the country? Detailed explanation of domestic Bitcoin purchase methods
Jul 30, 2025 pm 10:36 PM
How to buy Bitcoin in the country? Detailed explanation of domestic Bitcoin purchase methods
Jul 30, 2025 pm 10:36 PM
Domestic purchase of Bitcoin must be carried out through compliance channels, such as Hong Kong licensed exchanges or international compliance platforms; 2. Complete real-name authentication after registration, submit ID documents and address proof and perform facial recognition; 3. Prepare legal currency and recharge it to the trading account through bank transfer or electronic payment; 4. Log in to the platform to select Bitcoin trading pairs, set limit orders or market orders to complete the transaction; 5. Pay attention to market fluctuations and platform security, enable dual certification and comply with domestic regulatory policies; overall, investors should operate cautiously under the premise of compliance and participate in Bitcoin investment rationally.






