First introduce
<script src="js/md5.js?1.1.10" type="text/javascript"></script>
Usage:
hex_md5("123456");
md5.js file download:
/*
?*?A?JavaScript?implementation?of?the?RSA?Data?Security,?Inc.?MD5?Message
?*?Digest?Algorithm,?as?defined?in?RFC?1321.
?*?Version?2.1?Copyright?(C)?Paul?Johnston?1999?-?2002.
?*?Other?contributors:?Greg?Holt,?Andrew?Kepert,?Ydnar,?Lostinet
?*?Distributed?under?the?BSD?License
?*?See??for?more?info.?*//*
?*?Configurable?variables.?You?may?need?to?tweak?these?to?be?compatible?with
?*?the?server-side,?but?the?defaults?work?in?most?cases.?*/var?hexcase?=?0;??/*?hex?output?format.?0?-?lowercase;?1?-?uppercase????????*/var?b64pad??=?"";?/*?base-64?pad?character.?"="?for?strict?RFC?compliance???*/var?chrsz???=?8;??/*?bits?per?input?character.?8?-?ASCII;?16?-?Unicode??????*//*
?*?These?are?the?functions?you'll?usually?want?to?call
?*?They?take?string?arguments?and?return?either?hex?or?base-64?encoded?strings?*/function?hex_md5(s){?return?binl2hex(core_md5(str2binl(s),?s.length?*?chrsz));}
function?b64_md5(s){?return?binl2b64(core_md5(str2binl(s),?s.length?*?chrsz));}
function?str_md5(s){?return?binl2str(core_md5(str2binl(s),?s.length?*?chrsz));}
function?hex_hmac_md5(key,?data)?{?return?binl2hex(core_hmac_md5(key,?data));?}
function?b64_hmac_md5(key,?data)?{?return?binl2b64(core_hmac_md5(key,?data));?}
function?str_hmac_md5(key,?data)?{?return?binl2str(core_hmac_md5(key,?data));?}/*
?*?Perform?a?simple?self-test?to?see?if?the?VM?is?working?*/function?md5_vm_test()
{??return?hex_md5("abc")?==?"900150983cd24fb0d6963f7d28e17f72";
}/*
?*?Calculate?the?MD5?of?an?array?of?little-endian?words,?and?a?bit?length?*/function?core_md5(x,?len)
{??/*?append?padding?*/
??x[len?>>?5]?|=?0x80?<< ((len) % 32);
x[(((len + 64) >>>?9)?<< 4) + 14] = len; var a = 1732584193; var b = -271733879; var c = -1732584194; var d = 271733878; for(var i = 0; i < x.length; i += 16)
{var olda = a;var oldb = b;var oldc = c;var oldd = d;
a = md5_ff(a, b, c, d, x[i+ 0], 7 , -680876936);
d = md5_ff(d, a, b, c, x[i+ 1], 12, -389564586);
c = md5_ff(c, d, a, b, x[i+ 2], 17, 606105819);
b = md5_ff(b, c, d, a, x[i+ 3], 22, -1044525330);
a = md5_ff(a, b, c, d, x[i+ 4], 7 , -176418897);
d = md5_ff(d, a, b, c, x[i+ 5], 12, 1200080426);
c = md5_ff(c, d, a, b, x[i+ 6], 17, -1473231341);
b = md5_ff(b, c, d, a, x[i+ 7], 22, -45705983);
a = md5_ff(a, b, c, d, x[i+ 8], 7 , 1770035416);
d = md5_ff(d, a, b, c, x[i+ 9], 12, -1958414417);
c = md5_ff(c, d, a, b, x[i+10], 17, -42063);
b = md5_ff(b, c, d, a, x[i+11], 22, -1990404162);
a = md5_ff(a, b, c, d, x[i+12], 7 , 1804603682);
d = md5_ff(d, a, b, c, x[i+13], 12, -40341101);
c = md5_ff(c, d, a, b, x[i+14], 17, -1502002290);
b = md5_ff(b, c, d, a, x[i+15], 22, 1236535329);
a = md5_gg(a, b, c, d, x[i+ 1], 5 , -165796510);
d = md5_gg(d, a, b, c, x[i+ 6], 9 , -1069501632);
c = md5_gg(c, d, a, b, x[i+11], 14, 643717713);
b = md5_gg(b, c, d, a, x[i+ 0], 20, -373897302);
a = md5_gg(a, b, c, d, x[i+ 5], 5 , -701558691);
d = md5_gg(d, a, b, c, x[i+10], 9 , 38016083);
c = md5_gg(c, d, a, b, x[i+15], 14, -660478335);
b = md5_gg(b, c, d, a, x[i+ 4], 20, -405537848);
a = md5_gg(a, b, c, d, x[i+ 9], 5 , 568446438);
d = md5_gg(d, a, b, c, x[i+14], 9 , -1019803690);
c = md5_gg(c, d, a, b, x[i+ 3], 14, -187363961);
b = md5_gg(b, c, d, a, x[i+ 8], 20, 1163531501);
a = md5_gg(a, b, c, d, x[i+13], 5 , -1444681467);
d = md5_gg(d, a, b, c, x[i+ 2], 9 , -51403784);
c = md5_gg(c, d, a, b, x[i+ 7], 14, 1735328473);
b = md5_gg(b, c, d, a, x[i+12], 20, -1926607734);
a = md5_hh(a, b, c, d, x[i+ 5], 4 , -378558);
d = md5_hh(d, a, b, c, x[i+ 8], 11, -2022574463);
c = md5_hh(c, d, a, b, x[i+11], 16, 1839030562);
b = md5_hh(b, c, d, a, x[i+14], 23, -35309556);
a = md5_hh(a, b, c, d, x[i+ 1], 4 , -1530992060);
d = md5_hh(d, a, b, c, x[i+ 4], 11, 1272893353);
c = md5_hh(c, d, a, b, x[i+ 7], 16, -155497632);
b = md5_hh(b, c, d, a, x[i+10], 23, -1094730640);
a = md5_hh(a, b, c, d, x[i+13], 4 , 681279174);
d = md5_hh(d, a, b, c, x[i+ 0], 11, -358537222);
c = md5_hh(c, d, a, b, x[i+ 3], 16, -722521979);
b = md5_hh(b, c, d, a, x[i+ 6], 23, 76029189);
a = md5_hh(a, b, c, d, x[i+ 9], 4 , -640364487);
d = md5_hh(d, a, b, c, x[i+12], 11, -421815835);
c = md5_hh(c, d, a, b, x[i+15], 16, 530742520);
b = md5_hh(b, c, d, a, x[i+ 2], 23, -995338651);
a = md5_ii(a, b, c, d, x[i+ 0], 6 , -198630844);
d = md5_ii(d, a, b, c, x[i+ 7], 10, 1126891415);
c = md5_ii(c, d, a, b, x[i+14], 15, -1416354905);
b = md5_ii(b, c, d, a, x[i+ 5], 21, -57434055);
a = md5_ii(a, b, c, d, x[i+12], 6 , 1700485571);
d = md5_ii(d, a, b, c, x[i+ 3], 10, -1894986606);
c = md5_ii(c, d, a, b, x[i+10], 15, -1051523);
b = md5_ii(b, c, d, a, x[i+ 1], 21, -2054922799);
a = md5_ii(a, b, c, d, x[i+ 8], 6 , 1873313359);
d = md5_ii(d, a, b, c, x[i+15], 10, -30611744);
c = md5_ii(c, d, a, b, x[i+ 6], 15, -1560198380);
b = md5_ii(b, c, d, a, x[i+13], 21, 1309151649);
a = md5_ii(a, b, c, d, x[i+ 4], 6 , -145523070);
d = md5_ii(d, a, b, c, x[i+11], 10, -1120210379);
c = md5_ii(c, d, a, b, x[i+ 2], 15, 718787259);
b = md5_ii(b, c, d, a, x[i+ 9], 21, -343485551);
a = safe_add(a, olda);
b = safe_add(b, oldb);
c = safe_add(c, oldc);
d = safe_add(d, oldd);
} return Array(a, b, c, d);
}/*
* These functions implement the four basic operations the algorithm uses. */function md5_cmn(q, a, b, x, s, t)
{ return safe_add(bit_rol(safe_add(safe_add(a, q), safe_add(x, t)), s),b);
}
function md5_ff(a, b, c, d, x, s, t)
{ return md5_cmn((b & c) | ((~b) & d), a, b, x, s, t);
}
function md5_gg(a, b, c, d, x, s, t)
{ return md5_cmn((b & d) | (c & (~d)), a, b, x, s, t);
}
function md5_hh(a, b, c, d, x, s, t)
{ return md5_cmn(b ^ c ^ d, a, b, x, s, t);
}
function md5_ii(a, b, c, d, x, s, t)
{ return md5_cmn(c ^ (b | (~d)), a, b, x, s, t);
}/*
* Calculate the HMAC-MD5, of a key and some data */function core_hmac_md5(key, data)
{ var bkey = str2binl(key); if(bkey.length >?16)?bkey?=?core_md5(bkey,?key.length?*?chrsz);??var?ipad?=?Array(16),?opad?=?Array(16);??for(var?i?=?0;?i?< 16; i++)
{
ipad[i] = bkey[i] ^ 0x36363636;
opad[i] = bkey[i] ^ 0x5C5C5C5C;
} var hash = core_md5(ipad.concat(str2binl(data)), 512 + data.length * chrsz); return core_md5(opad.concat(hash), 512 + 128);
}/*
* Add integers, wrapping at 2^32. This uses 16-bit operations internally
* to work around bugs in some JS interpreters. */function safe_add(x, y)
{ var lsw = (x & 0xFFFF) + (y & 0xFFFF); var msw = (x >>?16)?+?(y?>>?16)?+?(lsw?>>?16);??return?(msw?<< 16) | (lsw & 0xFFFF);
}/*
* Bitwise rotate a 32-bit number to the left. */function bit_rol(num, cnt)
{ return (num << cnt) | (num >>>?(32?-?cnt));
}/*
?*?Convert?a?string?to?an?array?of?little-endian?words
?*?If?chrsz?is?ASCII,?characters?>255?have?their?hi-byte?silently?ignored.?*/function?str2binl(str)
{??var?bin?=?Array();??var?mask?=?(1?<< chrsz) - 1; for(var i = 0; i < str.length * chrsz; i += chrsz)
bin[i>>5]?|=?(str.charCodeAt(i?/?chrsz)?&?mask)?<< (i%32); return bin;
}/*
* Convert an array of little-endian words to a string */function binl2str(bin)
{ var str = ""; var mask = (1 << chrsz) - 1; for(var i = 0; i < bin.length * 32; i += chrsz)
str += String.fromCharCode((bin[i>>5]?>>>?(i?%?32))?&?mask);??return?str;
}/*
?*?Convert?an?array?of?little-endian?words?to?a?hex?string.?*/function?binl2hex(binarray)
{??var?hex_tab?=?hexcase???"0123456789ABCDEF"?:?"0123456789abcdef";??var?str?=?"";??for(var?i?=?0;?i?< binarray.length * 4; i++)
{
str += hex_tab.charAt((binarray[i>>2]?>>?((i%4)*8+4))?&?0xF)?+???hex_tab.charAt((binarray[i>>2]?>>?((i%4)*8??))?&?0xF);
??}??return?str;
}/*
?*?Convert?an?array?of?little-endian?words?to?a?base-64?string?*/function?binl2b64(binarray)
{??var?tab?=?"ABCDEFGHIJKLMNOPQRSTUVWXYZabcdefghijklmnopqrstuvwxyz0123456789+/";??var?str?=?"";??for(var?i?=?0;?i?< binarray.length * 4; i += 3)
{var triplet = (((binarray[i >>?2]?>>?8?*?(?i???%4))?&?0xFF)?<< 16)| (((binarray[i+1 >>?2]?>>?8?*?((i+1)%4))?&?0xFF)?<< 8 )| ((binarray[i+2 >>?2]?>>?8?*?((i+2)%4))?&?0xFF);for(var?j?=?0;?j?< 4; j++)
{ if(i * 8 + j * 6 >?binarray.length?*?32)?str?+=?b64pad;??????else?str?+=?tab.charAt((triplet?>>?6*(3-j))?&?0x3F);
????}
??}??return?str;
}The above is the detailed content of How to use md5 encryption in js. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undress AI Tool
Undress images for free

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)
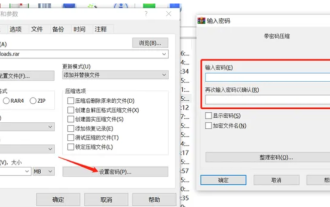 How to encrypt the compressed package in winrar-winrar encrypted compressed package method
Mar 23, 2024 pm 12:10 PM
How to encrypt the compressed package in winrar-winrar encrypted compressed package method
Mar 23, 2024 pm 12:10 PM
The editor will introduce to you three methods of encryption and compression: Method 1: Encryption The simplest encryption method is to enter the password you want to set when encrypting the file, and the encryption and compression are completed. Method 2: Automatic encryption Ordinary encryption method requires us to enter a password when encrypting each file. If you want to encrypt a large number of compressed packages and the passwords are the same, then we can set automatic encryption in WinRAR, and then just When compressing files normally, WinRAR will add a password to each compressed package. The method is as follows: Open WinRAR, click Options-Settings in the setting interface, switch to [Compression], click Create Default Configuration-Set Password Enter the password we want to set here, click OK to complete the setting, we only need to correct
 How to set a password for folder encryption without compression
Feb 20, 2024 pm 03:27 PM
How to set a password for folder encryption without compression
Feb 20, 2024 pm 03:27 PM
Folder encryption is a common data protection method that encrypts the contents of a folder so that only those who have the decryption password can access the files. When encrypting a folder, there are some common ways to set a password without compressing the file. First, we can use the encryption function that comes with the operating system to set a folder password. For Windows users, you can set it up by following the following steps: Select the folder to be encrypted, right-click the folder, and select "Properties"
 How to set up encryption of photo album on Apple mobile phone
Mar 02, 2024 pm 05:31 PM
How to set up encryption of photo album on Apple mobile phone
Mar 02, 2024 pm 05:31 PM
In Apple mobile phones, users can encrypt photo albums according to their own needs. Some users don't know how to set it up. You can add the pictures that need to be encrypted to the memo, and then lock the memo. Next, the editor will introduce the method of setting up the encryption of mobile photo albums for users. Interested users, come and take a look! Apple mobile phone tutorial How to set up iPhone photo album encryption A: After adding the pictures that need to be encrypted to the memo, go to lock the memo for detailed introduction: 1. Enter the photo album, select the picture that needs to be encrypted, and then click [Add to] below. 2. Select [Add to Notes]. 3. Enter the memo, find the memo you just created, enter it, and click the [Send] icon in the upper right corner. 4. Click [Lock Device] below
 Analog, a new project by crypto veterans: raised $16 million, with airdrop expected
Feb 22, 2024 pm 04:50 PM
Analog, a new project by crypto veterans: raised $16 million, with airdrop expected
Feb 22, 2024 pm 04:50 PM
Original author: Meteor, ChainCatcher Original editor: Marco, ChainCatcher Recently, the full-chain interoperability protocol Analog has entered the public eye with the disclosure of US$16 million in financing. Investment institutions include TribeCapital, NGCVentures, Wintermute, GSR, NEAR, OrangeDAO, and Mike Novogratz’s Alternative asset management companies Samara Asset Group, Balaji Srinivasan, etc. At the end of 2023, Analog caused some excitement in the industry. They released information on the open testnet registration event on the X platform.
 Which of the top ten virtual currency trading apps is the best? Which of the top ten virtual currency trading apps is the most reliable
Mar 19, 2025 pm 05:00 PM
Which of the top ten virtual currency trading apps is the best? Which of the top ten virtual currency trading apps is the most reliable
Mar 19, 2025 pm 05:00 PM
Top 10 virtual currency trading apps rankings: 1. OKX, 2. Binance, 3. Gate.io, 4. Kraken, 5. Huobi, 6. Coinbase, 7. KuCoin, 8. Crypto.com, 9. Bitfinex, 10. Gemini. Security, liquidity, handling fees, currency selection, user interface and customer support should be considered when choosing a platform.
 Get the gate.io installation package for free
Feb 21, 2025 pm 08:21 PM
Get the gate.io installation package for free
Feb 21, 2025 pm 08:21 PM
Gate.io is a popular cryptocurrency exchange that users can use by downloading its installation package and installing it on their devices. The steps to obtain the installation package are as follows: Visit the official website of Gate.io, click "Download", select the corresponding operating system (Windows, Mac or Linux), and download the installation package to your computer. It is recommended to temporarily disable antivirus software or firewall during installation to ensure smooth installation. After completion, the user needs to create a Gate.io account to start using it.
 How to decrypt the encrypted computer version of EZVIZ Cloud Video? -EZVIZ Cloud Video PC version exits full screen?
Mar 18, 2024 pm 12:25 PM
How to decrypt the encrypted computer version of EZVIZ Cloud Video? -EZVIZ Cloud Video PC version exits full screen?
Mar 18, 2024 pm 12:25 PM
How to de-encrypt videos on EZVIZ Cloud: There are many ways to de-encrypt videos on EZVIZ Cloud, one of which is by using the EZVIZ Cloud Mobile App. Users only need to enter the device list, select the camera to be decrypted and enter the device details page. On the device details page, find the "Settings" option, and then select "Video Encryption" to make relevant settings. In the video encryption settings interface, you can choose the option to turn off video encryption, and save the settings to complete the decryption operation. This simple step allows users to easily decrypt videos and improves the convenience of using the camera. If you use the computer client of EZVIZ Cloud, you can also cancel video encryption through similar steps. Just log in and select the corresponding camera, enter the device details interface, and then look for video addition in the settings.
 How to decrypt an encrypted folder
Feb 18, 2024 am 10:03 AM
How to decrypt an encrypted folder
Feb 18, 2024 am 10:03 AM
Folder encryption is a common way to protect personal and confidential files. When we need to protect certain files or folders from being accessed or viewed by others, we can choose to encrypt the folder. However, sometimes when we no longer need to encrypt a certain folder, we need to know how to unencrypt the folder. The method of decrypting a folder varies slightly depending on the operating system. In this article, I will introduce the steps to decrypt folders under Windows and Mac systems. For Windows systems: Open encrypted files






