 WeChat Applet
WeChat Applet
 WeChat Development
WeChat Development
 Why does WeChat payment verification or signature fail? Attached are three solutions
Why does WeChat payment verification or signature fail? Attached are three solutions
Why does WeChat payment verification or signature fail? Attached are three solutions
Aug 07, 2018 pm 03:44 PMWhy does iOS WeChat unified payment verification fail? I'm really anxious because my signature failed and I still can't pay. The main problem is that the body is in Chinese, which is very troublesome to solve. I searched a lot on Baidu, but I can't find any articles that completely solve it. In short, it's all kinds of troubles. I won’t go into details here, let’s get to the point:
Because the company’s projects require WeChat payment, during deployment, I found that signature errors were always reported. After investigation, it turned out to be a coding problem, so we will solve it if we find the reason. Question, this article introduces three solutions in detail. If you have limited time and don’t have time to read it, then go directly to the third solution. I hope it can help everyone.
The first solution: Set the tomcat encoding to utf-8
The default encoding of tomcat in the window environment is gbk, so set the tomcat encoding to utf-8.
Step 1: Add
set JAVA_OPTS=-Xms128m -Xmx512m -XX:MaxPermSize=256m -Dfile.encoding=utf-8 -Dsun.jnu.encoding=utf-8
讓java環(huán)境使用utf-8編碼
to the second line of the header in catalina.bat Step 2: Add
URIEncoding="UTF-8 to server.xml " useBodyEncodingForURI="true", causes the request sent by tomcat to use utf-8, as shown in the following code
##
connectionTimeout="20000"
##redirectPort="8443" URIEncoding="UTF-8" useBodyEncodingForURI=" true" />The console may have garbled characters, but it will be fine if changed to gbk, but the WeChat signature fails
##The second type Solution: Convert body
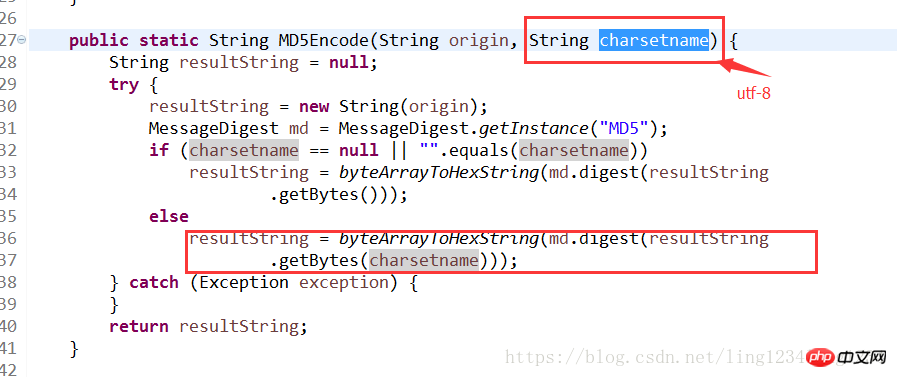 The third solution: modify the signature MD5 encoding (
The third solution: modify the signature MD5 encoding (
)
The default encoding of tomcat in the window environment is gbk, so when performing md5 signature, set the encoding to utf-8.
This is the MD5 signature tool class I use: 
public class MD5Util {
private static String byteArrayToHexString(byte b[]) {
StringBuffer resultSb = new StringBuffer();
for (int i = 0; i < b.length; i++)
resultSb.append(byteToHexString(b[i]));
return resultSb.toString();
}
private static String byteToHexString(byte b) {
int n = b;
if (n < 0)
n += 256;
int d1 = n / 16;
int d2 = n % 16;
return hexDigits[d1] + hexDigits[d2];
}
public static String MD5Encode(String origin, String charsetname) {
String resultString = null;
try {
resultString = new String(origin);
MessageDigest md = MessageDigest.getInstance("MD5");
if (charsetname == null || "".equals(charsetname))
resultString = byteArrayToHexString(md.digest(resultString
.getBytes()));
else
resultString = byteArrayToHexString(md.digest(resultString
.getBytes(charsetname)));
} catch (Exception exception) {
}
return resultString;
}
private static final String hexDigits[] = { "0", "1", "2", "3", "4", "5",
"6", "7", "8", "9", "a", "b", "c", "d", "e", "f" };
} Related recommendations:
WeChat app payment: payment permissions The check failed, why?
WeChat app payment: Payment permission check failed, what is the reason
The above is the detailed content of Why does WeChat payment verification or signature fail? Attached are three solutions. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undress AI Tool
Undress images for free

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)
 How to handle transactions in Java with JDBC?
Aug 02, 2025 pm 12:29 PM
How to handle transactions in Java with JDBC?
Aug 02, 2025 pm 12:29 PM
To correctly handle JDBC transactions, you must first turn off the automatic commit mode, then perform multiple operations, and finally commit or rollback according to the results; 1. Call conn.setAutoCommit(false) to start the transaction; 2. Execute multiple SQL operations, such as INSERT and UPDATE; 3. Call conn.commit() if all operations are successful, and call conn.rollback() if an exception occurs to ensure data consistency; at the same time, try-with-resources should be used to manage resources, properly handle exceptions and close connections to avoid connection leakage; in addition, it is recommended to use connection pools and set save points to achieve partial rollback, and keep transactions as short as possible to improve performance.
 JD Stablecoin Official Website Where to buy JD Stablecoin
Aug 01, 2025 pm 06:51 PM
JD Stablecoin Official Website Where to buy JD Stablecoin
Aug 01, 2025 pm 06:51 PM
Currently, JD.com has not issued any stablecoins, and users can choose the following platforms to purchase mainstream stablecoins: 1. Binance is the platform with the largest transaction volume in the world, supports multiple fiat currency payments, and has strong liquidity; 2. OKX has powerful functions, providing 7x24-hour customer service and multiple payment methods; 3. Huobi has high reputation in the Chinese community and has a complete risk control system; 4. Gate.io has rich currency types, suitable for exploring niche assets after purchasing stablecoins; 5. There are many types of currency listed on KuCoin, which is conducive to discovering early projects; 6. Bitget is characterized by order transactions, with convenient P2P transactions, and is suitable for social trading enthusiasts. The above platforms all provide safe and reliable stablecoin purchase services.
 How to work with Calendar in Java?
Aug 02, 2025 am 02:38 AM
How to work with Calendar in Java?
Aug 02, 2025 am 02:38 AM
Use classes in the java.time package to replace the old Date and Calendar classes; 2. Get the current date and time through LocalDate, LocalDateTime and LocalTime; 3. Create a specific date and time using the of() method; 4. Use the plus/minus method to immutably increase and decrease the time; 5. Use ZonedDateTime and ZoneId to process the time zone; 6. Format and parse date strings through DateTimeFormatter; 7. Use Instant to be compatible with the old date types when necessary; date processing in modern Java should give priority to using java.timeAPI, which provides clear, immutable and linear
 Comparing Java Frameworks: Spring Boot vs Quarkus vs Micronaut
Aug 04, 2025 pm 12:48 PM
Comparing Java Frameworks: Spring Boot vs Quarkus vs Micronaut
Aug 04, 2025 pm 12:48 PM
Pre-formanceTartuptimeMoryusage, Quarkusandmicronautleadduetocompile-Timeprocessingandgraalvsupport, Withquarkusoftenperforminglightbetterine ServerLess scenarios.2.Thyvelopecosyste,
 How does garbage collection work in Java?
Aug 02, 2025 pm 01:55 PM
How does garbage collection work in Java?
Aug 02, 2025 pm 01:55 PM
Java's garbage collection (GC) is a mechanism that automatically manages memory, which reduces the risk of memory leakage by reclaiming unreachable objects. 1.GC judges the accessibility of the object from the root object (such as stack variables, active threads, static fields, etc.), and unreachable objects are marked as garbage. 2. Based on the mark-clearing algorithm, mark all reachable objects and clear unmarked objects. 3. Adopt a generational collection strategy: the new generation (Eden, S0, S1) frequently executes MinorGC; the elderly performs less but takes longer to perform MajorGC; Metaspace stores class metadata. 4. JVM provides a variety of GC devices: SerialGC is suitable for small applications; ParallelGC improves throughput; CMS reduces
 Using HTML `input` Types for User Data
Aug 03, 2025 am 11:07 AM
Using HTML `input` Types for User Data
Aug 03, 2025 am 11:07 AM
Choosing the right HTMLinput type can improve data accuracy, enhance user experience, and improve usability. 1. Select the corresponding input types according to the data type, such as text, email, tel, number and date, which can automatically checksum and adapt to the keyboard; 2. Use HTML5 to add new types such as url, color, range and search, which can provide a more intuitive interaction method; 3. Use placeholder and required attributes to improve the efficiency and accuracy of form filling, but it should be noted that placeholder cannot replace label.
 Comparing Java Build Tools: Maven vs. Gradle
Aug 03, 2025 pm 01:36 PM
Comparing Java Build Tools: Maven vs. Gradle
Aug 03, 2025 pm 01:36 PM
Gradleisthebetterchoiceformostnewprojectsduetoitssuperiorflexibility,performance,andmoderntoolingsupport.1.Gradle’sGroovy/KotlinDSLismoreconciseandexpressivethanMaven’sverboseXML.2.GradleoutperformsMaveninbuildspeedwithincrementalcompilation,buildcac
 go by example defer statement explained
Aug 02, 2025 am 06:26 AM
go by example defer statement explained
Aug 02, 2025 am 06:26 AM
defer is used to perform specified operations before the function returns, such as cleaning resources; parameters are evaluated immediately when defer, and the functions are executed in the order of last-in-first-out (LIFO); 1. Multiple defers are executed in reverse order of declarations; 2. Commonly used for secure cleaning such as file closing; 3. The named return value can be modified; 4. It will be executed even if panic occurs, suitable for recovery; 5. Avoid abuse of defer in loops to prevent resource leakage; correct use can improve code security and readability.





