 Common Problem
Common Problem
 Interview with a big factory: HTTPS was asked three times in a row, and the last question was whether there are many people
Interview with a big factory: HTTPS was asked three times in a row, and the last question was whether there are many people
Interview with a big factory: HTTPS was asked three times in a row, and the last question was whether there are many people
Aug 28, 2023 pm 04:43 PMHello everyone, I am Lao Tian who specializes in sharing useful information with you. In addition, friends who need interview materials, remember to reply backstageInterview
##Preface
Everyone knows that HTTPS is more secure than HTTP. We have also heard of concepts related to the HTTPS protocol such as SSL, asymmetric encryption, CA certificates, etc.But you may not be able to answer the following three soul torture questions:
Why is HTTPS safe? How to implement the underlying principle of HTTPS? #Is using HTTPS necessarily safe?
The implementation principle of HTTPS
Everyone may have heard that the reason why the HTTPS protocol is secure is because HTTPS The protocol encrypts the transmitted data, and the encryption process is implemented using asymmetric encryption.But in fact, HTTPS uses symmetric encryption to encrypt content transmission, and asymmetric encryption only works in the certificate verification phase.
The overall process of HTTPS is divided into certificate verification and data transmission stages. The specific interaction process is as follows:
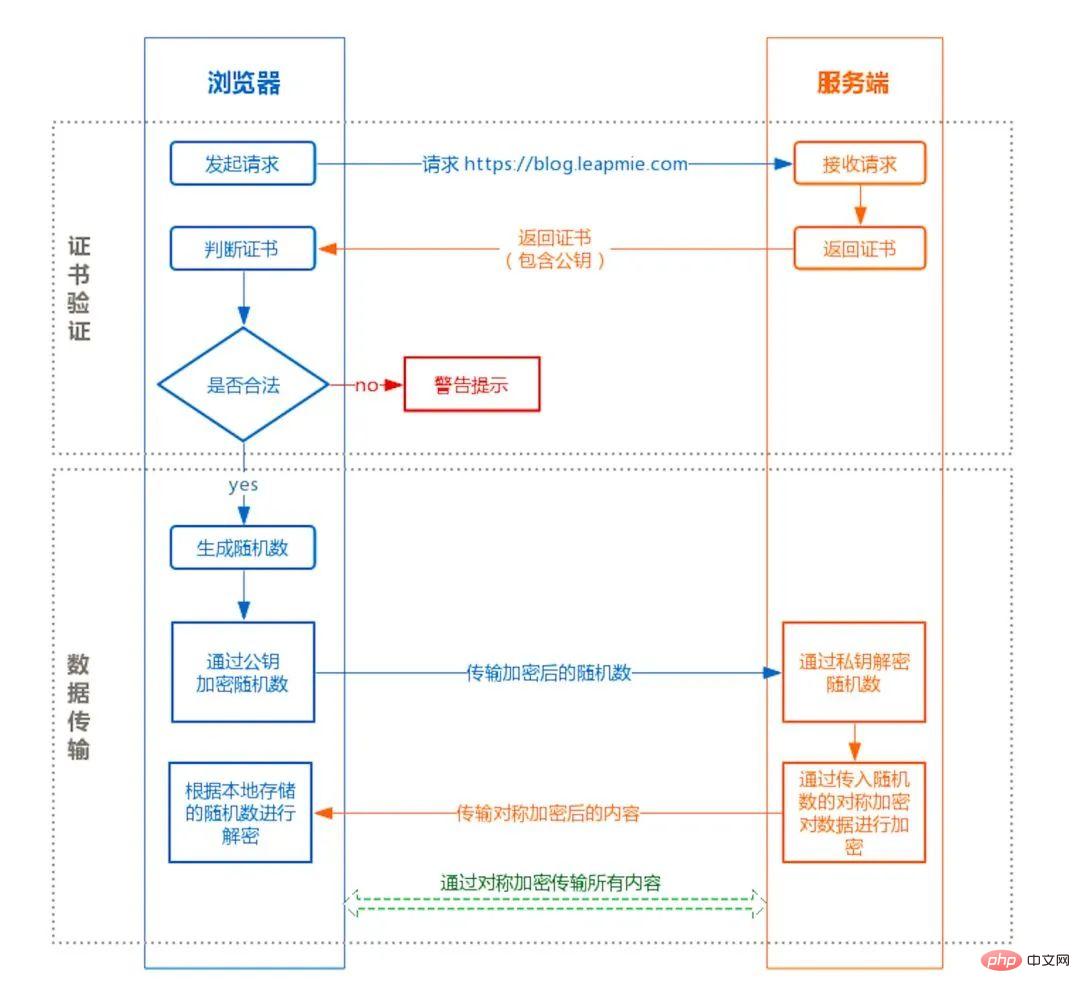
Certificate verification stage :
The browser initiates an HTTPS request. The server returns the HTTPS certificate. The client verifies whether the certificate is legal and prompts an alarm if it is not legal.
Data transmission phase:
When the certificate is verified to be legal, a random number is generated locally. Encrypt the random number through the public key and transmit the encrypted random number to the server. The server decrypts the random number through the private key. The server constructs a symmetric encryption algorithm through the random numbers passed in by the client, and encrypts the returned result content before transmitting it.
Why is symmetric encryption used for data transmission?
First of all, the encryption and decryption efficiency of asymmetric encryption is very low, and in HTTP application scenarios, there is usually a lot of interaction between ends, and asymmetric encryption The efficiency is unacceptable.
In addition, in the HTTPS scenario, only the server saves the private key, and a pair of public and private keys can only achieve one-way encryption and decryption. Therefore, the content transmission encryption in HTTPS adopts symmetric encryption instead of asymmetric encryption. encryption.
Why do we need a CA certification authority to issue a certificate?
The HTTP protocol is considered unsafe because the transmission process can easily be hooked by listeners to monitor and forge servers, while the HTTPS protocol mainly solves the security problem of network transmission. .
First of all, we assume that there is no certification authority and anyone can create a certificate. The security risk this brings is the classic "man-in-the-middle attack" problem.
The specific process of "man-in-the-middle attack" is as follows:
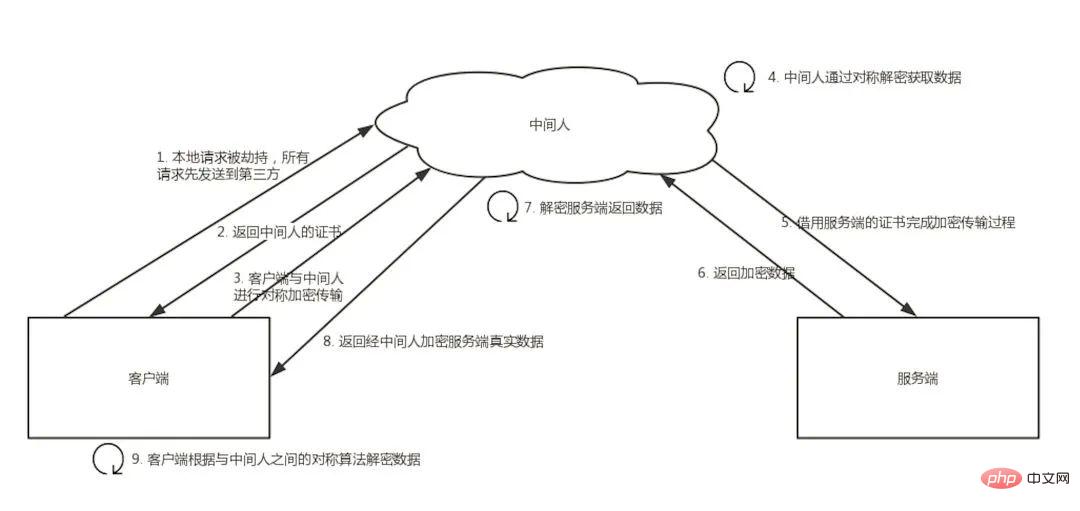
- Local requests are hijacked (such as DNS hijacking, etc.), and all requests are sent to the middleman's server.
- The middleman server returns the middleman's own certificate.
- The client creates a random number, encrypts the random number through the public key of the middleman certificate and transmits it to the middleman, and then uses the random number to construct symmetric encryption to encrypt the transmission content.
- Because the middleman has the client's random number, it can decrypt the content through a symmetric encryption algorithm.
- The middleman uses the client's request content to initiate a request to the regular website.
- Because the communication process between the middleman and the server is legal, the regular website returns encrypted data through the established secure channel.
- The middleman decrypts the content using a symmetric encryption algorithm established with the legitimate website.
- The middleman encrypts and transmits the data returned by the regular content through the symmetric encryption algorithm established with the client.
- The client decrypts the returned result data through the symmetric encryption algorithm established with the middleman.
The certificate contains the following information:
Issuing authority information Public key - ##Company information
- Domain name
- Validity period
- Fingerprint
- ......
First of all, the authoritative organization must be certified. Not just any organization is qualified to issue a certificate, otherwise it would not be called an authoritative organization. In addition, the credibility of the certificate is based on the trust system. The authoritative organization needs to endorse the certificate issued by it. As long as it is a certificate generated by an authoritative organization, we consider it to be legal. Therefore, authoritative organizations will review the applicant's information. Authoritative organizations at different levels have different review requirements, so certificates are also divided into free, cheap and expensive.
When the browser initiates an HTTPS request, the server will return the website's SSL certificate. The browser needs to perform the following verification on the certificate:
- Verify whether the domain name, validity period and other information are correct. The certificate contains this information, making it easier to complete the verification.
- Determine whether the certificate source is legal. Each issued certificate can find the corresponding root certificate according to the verification chain. The operating system and browser will store the root certificate of the authoritative organization locally. The local root certificate can be used to complete the source verification of the certificate issued by the corresponding organization.
** Determine whether the certificate has been tampered with. **Requires verification with CA server. #** Determine whether the certificate has been revoked. **Achieved through CRL (Certificate Revocation List) and OCSP (Online Certificate Status Protocol). OCSP can be used in step 3 to reduce interaction with the CA server and improve verification efficiency.
The browser will consider the certificate to be legitimate only if any of the above steps are met.
**Insert a question here that I have thought about for a long time but the answer is actually very simple: **Since the certificate is public, if I want to launch a man-in-the-middle attack, I download a certificate from the official website as my server certificate, then the client will definitely agree that this certificate is legitimate. How to avoid this kind of certificate fraud?
In fact, this is the use of public and private keys in non-encrypted symmetry. Although the middleman can obtain the certificate, the private key cannot be obtained.
It is impossible to deduce the corresponding private key from a public key. Even if the middleman obtains the certificate, it cannot pretend to be a legitimate server because it cannot decrypt the encrypted data passed in by the client.
Can only certification authorities generate certificates?
If you need the browser not to prompt for security risks, you can only use certificates issued by certification authorities.
But browsers usually only prompt for security risks and do not restrict the website from being accessible, so technically anyone can generate a certificate, and as long as there is a certificate, the HTTPS transmission of the website can be completed.
For example, the early 12306 used manual installation of private certificates to achieve HTTPS access.
What should I do if the local random number is stolen?
Certificate verification is implemented using asymmetric encryption, but the transmission process uses symmetric encryption, and the important random numbers in the symmetric encryption algorithm are locally generated and stored locally Yes, how does HTTPS ensure that the random number will not be stolen?
In fact, HTTPS does not include security guarantees for random numbers. HTTPS only guarantees the security of the transmission process, and the random numbers are stored locally. Local security belongs to another security category. The countermeasures include installing anti-virus software, Anti-Trojan horses, browser upgrades to fix vulnerabilities, etc.
Will the packet be captured if I use HTTPS?
HTTPS data is encrypted. Under normal circumstances, the packet content captured by the packet capture tool after proxy request is encrypted and cannot be viewed directly.
However, as mentioned above, the browser will only prompt the security risk. If the user authorizes it, he can still continue to access the website and complete the request.
Therefore, as long as the client is our own terminal and we authorize it, we can set up a middleman network, and the packet capture tool serves as the agent of the middleman.
Usually, the HTTPS packet capture tool is used to generate a certificate. The user needs to manually install the certificate into the client, and then all requests initiated by the terminal complete the interaction with the packet capture tool through this certificate.
Then the packet capture tool forwards the request to the server, and finally outputs the result returned by the server to the console and then returns it to the terminal, thereby completing the closed loop of the entire request.
Since HTTPS cannot prevent packet capture, what is the point of HTTPS? HTTPS can prevent users from being monitored on communication links without their knowledge. It does not provide protection for active credit-granting packet capture operations because users in this scenario are already aware of the risks.
To prevent packet capture, application-level security protection needs to be adopted, such as private symmetric encryption, and anti-decompilation reinforcement on the mobile terminal to prevent local algorithms from being cracked.
##Summary
The following is a brief Q&A summary of the full text:Q: Why is HTTPS safe?
A: Because HTTPS ensures transmission security, prevents the transmission process from being monitored, prevents data from being stolen, and can confirm the authenticity of the website.Q: What is the transmission process of HTTPS?
A: The client initiates an HTTPS request, the server returns a certificate, the client verifies the certificate, and after passing the verification, it locally generates a random number used to modify the symmetric encryption algorithm. The random number is encrypted and transmitted to the server through the public key in the certificate. After receiving it, the server decrypts the random number through the private key. Subsequent data interactions are encrypted and decrypted through the symmetric encryption algorithm.Q: Why do I need a certificate?
A: Prevent "man-in-the-middle" attacks and provide identity proof for the website.Q: Will packets be captured when using HTTPS?
A: Packets will be captured. HTTPS only prevents users from being monitored without their knowledge. If the user actively grants credit, a "middleman" network can be built, and the proxy software can monitor the transmitted content. Decrypt. I would like to share a process diagram of learning HTTPS: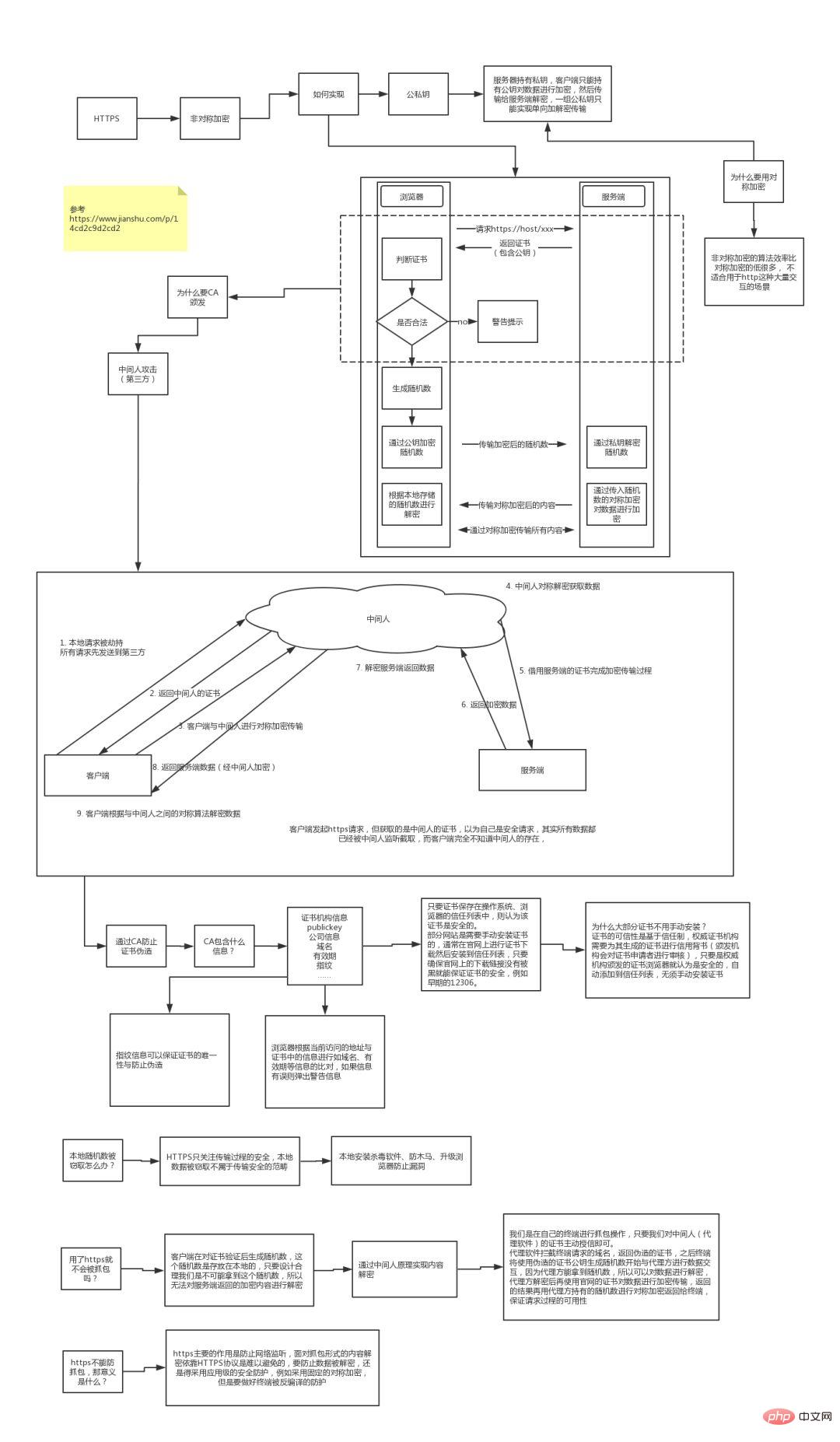
The above is the detailed content of Interview with a big factory: HTTPS was asked three times in a row, and the last question was whether there are many people. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undress AI Tool
Undress images for free

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)
 How to use Nginx Proxy Manager to implement automatic jump from HTTP to HTTPS
Sep 26, 2023 am 11:19 AM
How to use Nginx Proxy Manager to implement automatic jump from HTTP to HTTPS
Sep 26, 2023 am 11:19 AM
How to use NginxProxyManager to implement automatic jump from HTTP to HTTPS. With the development of the Internet, more and more websites are beginning to use the HTTPS protocol to encrypt data transmission to improve data security and user privacy protection. Since the HTTPS protocol requires the support of an SSL certificate, certain technical support is required when deploying the HTTPS protocol. Nginx is a powerful and commonly used HTTP server and reverse proxy server, and NginxProxy
 How to use Nginx Proxy Manager to implement reverse proxy under HTTPS protocol
Sep 26, 2023 am 08:40 AM
How to use Nginx Proxy Manager to implement reverse proxy under HTTPS protocol
Sep 26, 2023 am 08:40 AM
How to use NginxProxyManager to implement reverse proxy under HTTPS protocol. In recent years, with the popularity of the Internet and the diversification of application scenarios, the access methods of websites and applications have become more and more complex. In order to improve website access efficiency and security, many websites have begun to use reverse proxies to handle user requests. The reverse proxy for the HTTPS protocol plays an important role in protecting user privacy and ensuring communication security. This article will introduce how to use NginxProxy
 Nginx with SSL: Configure HTTPS to protect your web server
Jun 09, 2023 pm 09:24 PM
Nginx with SSL: Configure HTTPS to protect your web server
Jun 09, 2023 pm 09:24 PM
Nginx is a high-performance web server software and a powerful reverse proxy server and load balancer. With the rapid development of the Internet, more and more websites are beginning to use the SSL protocol to protect sensitive user data, and Nginx also provides powerful SSL support, making the security performance of the web server even further. This article will introduce how to configure Nginx to support the SSL protocol and protect the security performance of the web server. What is SSL protocol? SSL (SecureSocket
 How to configure https in tomcat
Jan 05, 2024 pm 05:15 PM
How to configure https in tomcat
Jan 05, 2024 pm 05:15 PM
Configuration steps: 1. Obtain the SSL certificate; 2. Configure the SSL certificate; 3. Edit the Tomcat configuration file; 4. Restart Tomcat. Detailed introduction: 1. You need to obtain an SSL certificate, either a self-signed certificate or a valid SSL certificate from a certification agency (such as Let's Encrypt); 2. Place the obtained SSL certificate and private key files on the server and ensure that these files Located in a safe location, only users with sufficient permissions can access; 3. Edit Tomcat configuration files, etc.
 Solution: urllib3 ProxySchemeUnknown(proxy.scheme)
Feb 29, 2024 pm 07:01 PM
Solution: urllib3 ProxySchemeUnknown(proxy.scheme)
Feb 29, 2024 pm 07:01 PM
The reason for the error is that the ProxySchemeUnknown(proxy.scheme) error of urllib3 is usually caused by the use of an unsupported proxy protocol. In this case, urllib3 does not recognize the proxy server's protocol type and therefore cannot use the proxy for network connections. To resolve this issue, you need to ensure that you are using a supported proxy protocol, such as HTTP or https. How to resolve To resolve this issue, you need to ensure that you are using a supported proxy protocol, such as HTTP or HTTPS. You can solve this problem by setting the proxy parameters of urllib3. If you are using an http proxy, the code example is as follows: importurllib3http
 How to set up a secure HTTPS connection for a PHP form?
Aug 17, 2023 pm 03:25 PM
How to set up a secure HTTPS connection for a PHP form?
Aug 17, 2023 pm 03:25 PM
How to set up a secure HTTPS connection for a PHP form? As the Internet develops, security becomes more and more important in web development. The encrypted transmission protocol HTTPS plays a key role in protecting data transmission. When using PHP forms for data transmission, we can take some measures to ensure the security of the connection. This article will guide you on how to set up a secure HTTPS connection for PHP forms, with some code examples. Purchase an SSL Certificate First, you need to purchase an SSL Certificate. SSL certificate is a guaranteed website
 Using HTTPS for data transmission in Java API development
Jun 18, 2023 pm 10:43 PM
Using HTTPS for data transmission in Java API development
Jun 18, 2023 pm 10:43 PM
With the development of science and technology, network communication has become one of the important tools for information transmission in modern society. But at the same time, information transmission on the network faces the risk of malicious attacks and theft, so security is particularly important. Based on this, the HTTPS protocol came into being. It is a protocol that adds SSL/TLS encryption to the HTTP protocol to ensure network transmission security. As a language widely used in network development, Java naturally provides a rich API to support the HTTPS protocol. This article will
 What does the https workflow look like?
Apr 07, 2024 am 09:27 AM
What does the https workflow look like?
Apr 07, 2024 am 09:27 AM
The https workflow includes steps such as client-initiated request, server response, SSL/TLS handshake, data transmission, and client-side rendering. Through these steps, the security and integrity of data during transmission can be ensured.




