Key Cybersecurity Challenges In 2025—Trends And Observations
Apr 08, 2025 pm 01:51 PM2025: Navigating the Evolving Cybersecurity Landscape
The cybersecurity landscape in 2025 is marked by a convergence of advanced technologies and persistent threats. This year presents unique challenges, demanding proactive and multifaceted security strategies.

The Rise of AI-Powered Threats:
A recent SoSafe study reveals a startling statistic: 87% of security professionals reported encountering AI-driven cyberattacks in the past year. The sophistication of AI agents, capable of complex tasks and autonomous actions, presents a significant concern. These agents can readily identify vulnerabilities, compromise systems, and exfiltrate sensitive data, posing a substantial threat to businesses and organizations. This mirrors the rapid adoption of generative AI tools like ChatGPT, which similarly disrupted the market in 2022.
However, the same AI technology offers powerful defensive capabilities. Agentic AI in cybersecurity can automate threat detection, response, and remediation, significantly reducing response times and analyst workload. The integration of generative AI (GenAI) and predictive algorithms promises even more effective threat prediction and mitigation strategies.

Healthcare: A Persistent Target:
The healthcare sector remains a prime target for cybercriminals. 2024 saw a record-breaking 276,775,457 compromised healthcare records—a 64.1% increase from the previous year. This underscores the urgent need for robust security measures, including multi-factor authentication, employee training, and layered security systems. Protecting patient data, medical devices, and network infrastructure is paramount.

The Quantum Computing Threat:
The emergence of quantum computing presents a new level of cybersecurity risk. Quantum computers, with their superior processing power, could potentially break current encryption standards, rendering existing security measures obsolete. The potential for widespread data breaches is a serious concern, particularly for financial systems and critical infrastructure. The arrival of "Q-Day," when quantum computers can easily crack public key systems, is looming closer than anticipated. Preparing for this eventuality requires a shift towards quantum-resistant cryptography and proactive security strategies.

Securing Space Assets:
The increasing reliance on space-based assets for communication, surveillance, and various other applications necessitates robust cybersecurity measures. Satellites and ground control centers are vulnerable to cyberattacks, highlighting the need for sophisticated security protocols and defenses. The growing number of satellites in orbit expands the potential attack surface, making space cybersecurity a critical area of focus.

The Persistent Threat of Ransomware:
Ransomware attacks remain a major concern, with AI-powered phishing attacks and social engineering techniques exacerbating the problem. The increasing sophistication of ransomware groups and the high cost of attacks necessitate improved preparedness and robust incident response plans. Small businesses, healthcare providers, and educational institutions are particularly vulnerable.

The Rise of DDoS Attacks:
Distributed Denial-of-Service (DDoS) attacks are on the rise, with DDoS-for-hire services becoming increasingly sophisticated. The use of DDoS attacks in cyber warfare and extortion schemes underscores the need for robust mitigation strategies and network security solutions.
Conclusion:
2025 presents a complex cybersecurity landscape, with both new and persistent threats. The convergence of AI, quantum computing, and the increasing reliance on interconnected systems demands a proactive and multi-layered approach to security. Organizations must invest in advanced security technologies, employee training, and robust incident response plans to effectively mitigate these risks and protect their valuable assets.
The above is the detailed content of Key Cybersecurity Challenges In 2025—Trends And Observations. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undress AI Tool
Undress images for free

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)
 Kimi K2: The Most Powerful Open-Source Agentic Model
Jul 12, 2025 am 09:16 AM
Kimi K2: The Most Powerful Open-Source Agentic Model
Jul 12, 2025 am 09:16 AM
Remember the flood of open-source Chinese models that disrupted the GenAI industry earlier this year? While DeepSeek took most of the headlines, Kimi K1.5 was one of the prominent names in the list. And the model was quite cool.
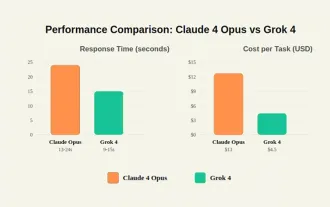 Grok 4 vs Claude 4: Which is Better?
Jul 12, 2025 am 09:37 AM
Grok 4 vs Claude 4: Which is Better?
Jul 12, 2025 am 09:37 AM
By mid-2025, the AI “arms race” is heating up, and xAI and Anthropic have both released their flagship models, Grok 4 and Claude 4. These two models are at opposite ends of the design philosophy and deployment platform, yet they
 10 Amazing Humanoid Robots Already Walking Among Us Today
Jul 16, 2025 am 11:12 AM
10 Amazing Humanoid Robots Already Walking Among Us Today
Jul 16, 2025 am 11:12 AM
But we probably won’t have to wait even 10 years to see one. In fact, what could be considered the first wave of truly useful, human-like machines is already here. Recent years have seen a number of prototypes and production models stepping out of t
 Leia's Immersity Mobile App Brings 3D Depth To Everyday Photos
Jul 09, 2025 am 11:17 AM
Leia's Immersity Mobile App Brings 3D Depth To Everyday Photos
Jul 09, 2025 am 11:17 AM
Built on Leia’s proprietary Neural Depth Engine, the app processes still images and adds natural depth along with simulated motion—such as pans, zooms, and parallax effects—to create short video reels that give the impression of stepping into the sce
 Context Engineering is the 'New' Prompt Engineering
Jul 12, 2025 am 09:33 AM
Context Engineering is the 'New' Prompt Engineering
Jul 12, 2025 am 09:33 AM
Until the previous year, prompt engineering was regarded a crucial skill for interacting with large language models (LLMs). Recently, however, LLMs have significantly advanced in their reasoning and comprehension abilities. Naturally, our expectation
 What Are The 7 Types Of AI Agents?
Jul 11, 2025 am 11:08 AM
What Are The 7 Types Of AI Agents?
Jul 11, 2025 am 11:08 AM
Picture something sophisticated, such as an AI engine ready to give detailed feedback on a new clothing collection from Milan, or automatic market analysis for a business operating worldwide, or intelligent systems managing a large vehicle fleet.The
 These AI Models Didn't Learn Language, They Learned Strategy
Jul 09, 2025 am 11:16 AM
These AI Models Didn't Learn Language, They Learned Strategy
Jul 09, 2025 am 11:16 AM
A new study from researchers at King’s College London and the University of Oxford shares results of what happened when OpenAI, Google and Anthropic were thrown together in a cutthroat competition based on the iterated prisoner's dilemma. This was no
 Concealed Command Crisis: Researchers Game AI To Get Published
Jul 13, 2025 am 11:08 AM
Concealed Command Crisis: Researchers Game AI To Get Published
Jul 13, 2025 am 11:08 AM
Scientists have uncovered a clever yet alarming method to bypass the system. July 2025 marked the discovery of an elaborate strategy where researchers inserted invisible instructions into their academic submissions — these covert directives were tail






