Found a total of 10000 related content

The value of Debian Sniffer in network performance evaluation
Article Introduction:This article discusses the application value of DebianSniffer (also known as Snort) in network performance evaluation. Although Sniffer is mainly used for network security, its traffic analysis capabilities make it a powerful tool for network performance evaluation. Key functions and values: 1. Network traffic analysis: Real-time monitoring: Sniffer can capture and analyze network packets to reveal traffic patterns, peaks and potential bottlenecks. Bandwidth utilization: Through packet analysis, accurately calculate bandwidth utilization and understand the network's data transmission speed at different times. 2. Performance evaluation: latency and packet loss: Although not its main function, Sniffer can provide network latency and packet loss rate information, which are crucial for performance evaluation.
2025-04-12
comment 0
533

How to Install Cacti on Rocky Linux and AlmaLinux
Article Introduction:Cacti is an open-source web-based network monitoring and graphing tool written in PHP. It was designed as a front-end application for data logging using RRDtool. Cacti uses the SNMP protocol to monitor devices such as routers, servers, and switches.
2025-07-08
comment 0
954

The role of Debian Sniffer in DDoS attack detection
Article Introduction:This article discusses the DDoS attack detection method. Although no direct application case of "DebianSniffer" was found, the following methods can be used for DDoS attack detection: Effective DDoS attack detection technology: Detection based on traffic analysis: identifying DDoS attacks by monitoring abnormal patterns of network traffic, such as sudden traffic growth, surge in connections on specific ports, etc. This can be achieved using a variety of tools, including but not limited to professional network monitoring systems and custom scripts. For example, Python scripts combined with pyshark and colorama libraries can monitor network traffic in real time and issue alerts. Detection based on statistical analysis: By analyzing statistical characteristics of network traffic, such as data
2025-04-12
comment 0
1029
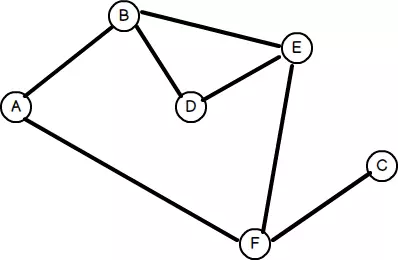
PHP Master | Data Structures for PHP Devs: Graphs
Article Introduction:Key Takeaways
Graphs are mathematical constructs used to model relationships between key/value pairs and have numerous real-world applications such as network optimization, traffic routing, and social network analysis. They are made up of vertices
2025-02-23
comment 0
936
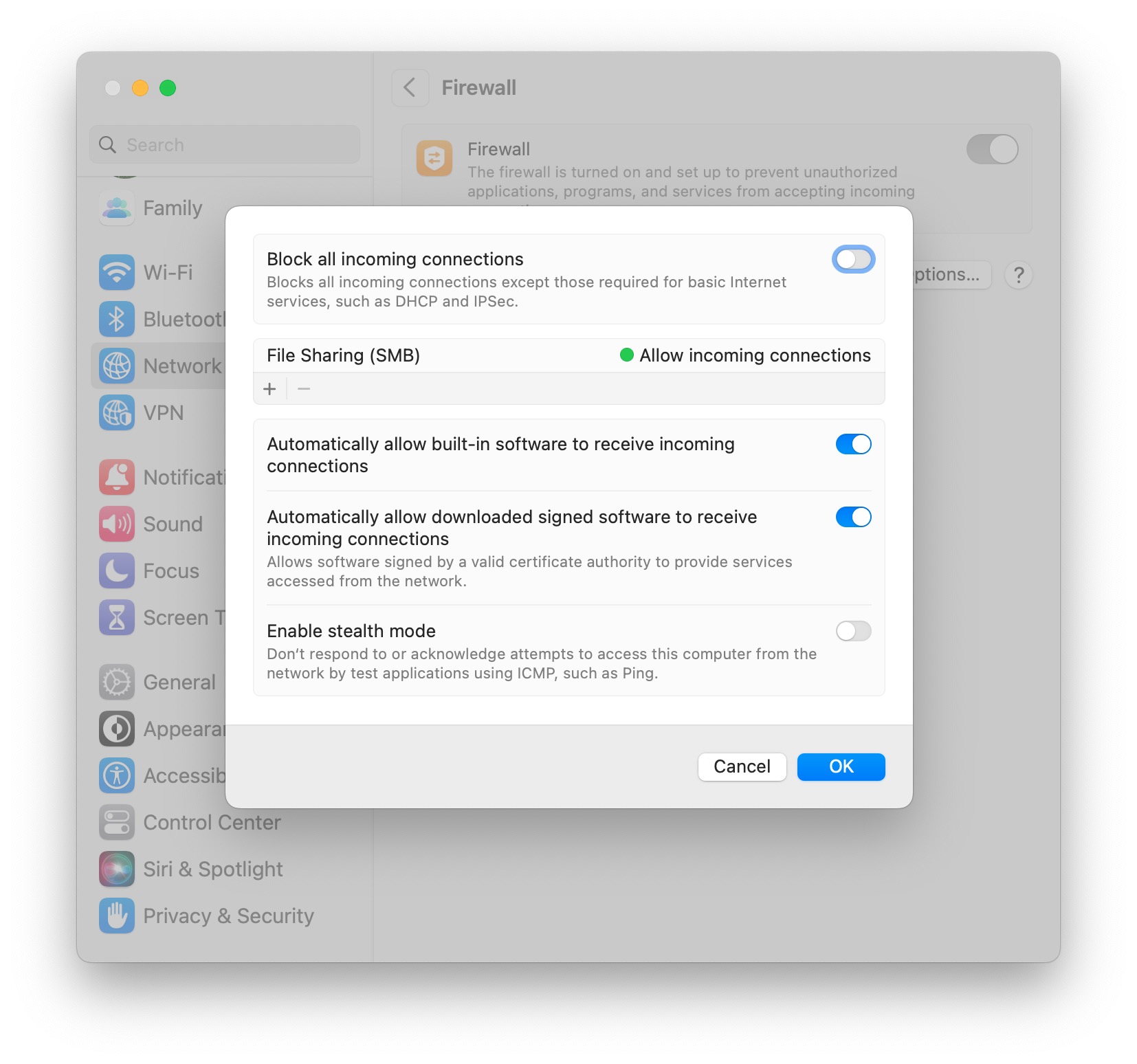
How to Enable or Disable Firewall on MacOS Ventura
Article Introduction:Firewalls function as a network security tool to observe and manage incoming and outgoing traffic to your computer and network, or the internet. MacOS comes equipped with a built-in software firewall that users can activate manually if they desire to
2025-06-06
comment 0
382


Comparison between Debian Sniffer and Wireshark
Article Introduction:This article discusses the network analysis tool Wireshark and its alternatives in Debian systems. It should be clear that there is no standard network analysis tool called "DebianSniffer". Wireshark is the industry's leading network protocol analyzer, while Debian systems offer other tools with similar functionality. Functional Feature Comparison Wireshark: This is a powerful network protocol analyzer that supports real-time network data capture and in-depth viewing of data packet content, and provides rich protocol support, filtering and search functions to facilitate the diagnosis of network problems. Alternative tools in the Debian system: The Debian system includes networks such as tcpdump and tshark
2025-04-12
comment 0
949

What does DeepSeek deep thinking and online search mean
Article Introduction:DeepSeekAI tool in-depth analysis: Deep thinking and network search function detailed explanation DeepSeek is a powerful AI intelligent interactive tool. This article will focus on its two core functions of "deep thinking" and "network search", helping you better understand and Use this tool. Interpretation of DeepSeek's core functions: Deep Thinking: DeepSeek's "deep thinking" function is not a simple information retrieval, but is based on a huge pre-trained knowledge base and powerful logical reasoning capabilities to conduct multi-dimensional and structured analysis of complex problems. It simulates human thinking patterns, provides logically rigorous and organized answers efficiently and comprehensively, and can effectively avoid emotional prejudice. Internet search: "Internet search" function
2025-02-19
comment 0
1368

Introducing NetIrk: A Lightweight CLI Tool for High-Level Network Insights
Article Introduction:Netirk is a lightweight and efficient CLI tool designed to perform high-level network analysis. Built with simplicity in mind, it offers essential features like connectivity checks, DNS tracing, and a lightweight server to test local networking setup
2025-01-03
comment 0
1071

The importance of Debian Sniffer in network monitoring
Article Introduction:Although the search results do not directly mention "DebianSniffer" and its specific application in network monitoring, we can infer that "Sniffer" refers to a network packet capture analysis tool, and its application in the Debian system is not essentially different from other Linux distributions. Network monitoring is crucial to maintaining network stability and optimizing performance, and packet capture analysis tools play a key role. The following explains the important role of network monitoring tools (such as Sniffer running in Debian systems): The value of network monitoring tools: Fast fault location: Real-time monitoring of network metrics, such as bandwidth usage, latency, packet loss rate, etc., which can quickly identify the root cause of network failures and shorten the troubleshooting time.
2025-04-12
comment 0
454

CentOS Stream 8 Firewall Setting Tutorial
Article Introduction:CentOSStream8 Firewall Management Guide: Use firewalld to finely control network access CentOSStream8 system uses firewalld as a dynamic firewall management tool, which defines the security level of different network traffic using the concept of "zones". This guide will gradually explain the basic configuration and management methods of firewalld. 1. Install firewalld If firewalld is not installed, please execute the following command: sudodnfinstallfirewalld 2. Start and status check Start the firewalld service: sudosystemctlstartfi
2025-04-14
comment 0
468

How to use the network inspector in Safari's developer tools?
Article Introduction:To open Safari's Network panel for network request debugging, please follow the following steps: 1. Open Safari → Preferences → Advanced → Check "Show the 'Development' menu in the menu bar"; 2. Open the landing page, click "Development" → "Show JavaScript Console" in the top menu bar (or use the shortcut key Option ? C); 3. Click the "Network" tab in the developer tool interface to enter the network panel. After refreshing the page, you can view the Name, Status, Type, Size and Time information of all loaded resources, and support clicking to view details, filtering classification, sorting by time, and recording network behavior for performance analysis and optimization judgment.
2025-07-12
comment 0
780

What are the virtual currency inquiry websites?
Article Introduction:As the cryptocurrency market develops, virtual currency inquiry websites have become a valuable tool for understanding the prices and dynamics of crypto assets. This article provides an authoritative ranking of the ten best virtual currency query websites based on website traffic, data accuracy, functionality and user experience, including CoinMarketCap, CoinGecko, Binance, Cointelegraph, messari, Nomics, CryptoCompare, LunarCrush, CoinPaprika and CryptoQuant. These sites provide investors with real-time prices, historical data, social sentiment analysis and institutional-grade indicators to help them make informed investment decisions
2024-11-21
comment 0
513

What is iptables and how do you use it to configure a firewall?
Article Introduction:Iptables is a powerful firewall tool in Linux systems, which controls network traffic in and out of the system by setting IP packet filtering rules. 1. It matches and processes data packets based on rule chains (INPUT, OUTPUT, FORWARD). The default policy is usually set to DROP to improve security. 2. When setting basic rules, you should first allow key services such as SSH, HTTP and HTTPS, and then block all other input traffic. 3. Use iptables-save and iptables-restore to achieve rule persistence. 4. Use -L-n-v to view rules, and delete or insert rules can be specified by line number. 5. Common uses include blocking suspicious IPs and allowing connections
2025-06-25
comment 0
718

Fault-Tolerant SFTP scripting - Retry Failed Transfers Automatically
Article Introduction:introduction
Modern network architectures are built on unreliable transmission media. The routing device can discard, corrupt, reorder or copy forwarded data at will. The IP layer in the TCP/IP protocol stack understands that it cannot guarantee the accuracy of data. No IP network can claim that it is 100% reliable.
The TCP layer acts as the guardian above the IP layer to ensure that the data it generates is correct. This is achieved through a variety of techniques, and sometimes data is deliberately lost to determine network limitations. Most people probably know that TCP provides a connection-based network on top of IP connectivity-free networks (which can and do discard traffic at will) and guarantees data delivery.
Interestingly, our file transfer tool is not as powerful as it is when facing a disconnected TCP connection.
2025-03-18
comment 0
598

What are the best practices for JavaScript development on Debian
Article Introduction:When developing JavaScript on Debian systems, you can use the following best practices to optimize the development process: Choosing the right log library is crucial for Node.js applications, choosing a powerful log library. Commonly used log libraries such as Winston, Pino and Bunyan provide rich functions, including log-level settings, formatting and storage. Using the correct log level Use the log level correctly (such as fatal, error, warn, info, debug) can help distinguish between critical events and general information events, and help with subsequent troubleshooting and performance optimization. Log analysis tool GoAccess: For network log analysis, GoAccess is a
2025-05-16
comment 0
429

Cursor Disappears on Mac: Why is Mouse not Showing Up?
Article Introduction:Quick solution to disappearing the Mac mouse cursor and root cause analysis
Your Mac cursor suddenly disappears and cannot be displayed even if you move the mouse or click? Don't worry, this article will provide a series of quick fixes and in-depth analysis to help you retrieve your disappearing cursor.
First, try some simple actions: right-click, click and drag anywhere on the screen, or check whether the network connection is stable (weak networks may cause cursor abnormality).
MacKeeper's Find and Repair tool is just the first step. Let's dive into the reasons and solutions for the disappearance of the Mac mouse cursor.
Reasons for the Mac mouse cursor disappearing:
Multi-monitor settings: The cursor may be lost when moving between monitors, check other screens and corners of the screen. Monitor settings
2025-04-03
comment 0
863

How to make money in deepseek
Article Introduction:DeepSeek: AI empowers, and gold-nuggles in a new era! As an AI intelligent network tool that has become popular all over the world, how can DeepSeek use it to achieve profitability? This article will reveal a variety of profit models to you, helping you seize opportunities and embark on a journey of wealth! DeepSeek profit strategy: high-risk and high-return investment: Use DeepSeek to assist in analyzing market trends and conduct short-term trading of stocks or cryptocurrencies. Be careful when operating, strictly control risks, and set stop loss points. Entrepreneurship and side business: DeepSeek helps private domain traffic operations, live streaming and knowledge payment. You can quickly accumulate customers and realize monetization through community operations, high-frequency live broadcasts or online courses. Arbitrage and information difference: Using DeepSeek high
2025-02-19
comment 0
874

What are some popular third-party Python libraries (e.g., NumPy, pandas, matplotlib, requests, Django, Flask)?
Article Introduction:Python's third-party library ecosystem is powerful and diverse, with cores including: 1. NumPy and Pandas are used for data processing and analysis, NumPy supports multi-dimensional array and matrix operations, Pandas provides DataFrame structure to simplify structured data operations; 2. Matplotlib and Seaborn are used for data visualization, the former is a basic drawing tool, and the latter provides more advanced statistical charts based on this; 3. Django and Flask are used for web development, Django functions are fully suitable for large applications, Flask is lightweight and flexible for small services or APIs; 4. Requests are used for HTTP requests, and handle network data interactions concisely and efficiently. These libraries each perform their own
2025-06-30
comment 0
205


















