 Java
Java
 javaTutorial
javaTutorial
 How to finely control the access_token interface access permissions through the scope mechanism of OAuth2.0?
How to finely control the access_token interface access permissions through the scope mechanism of OAuth2.0?
How to finely control the access_token interface access permissions through the scope mechanism of OAuth2.0?
Apr 19, 2025 pm 05:54 PM
Use access_token in OAuth 2.0 to finely control API access permissions
OAuth2.0 is widely used in modern application development, especially in the scenario of sharing user data across applications. For example, Company A's App nests Company B's H5 page, which requires access to Company A's user information. Company B obtained the access_token of Company A through OAuth2.0. How to ensure that this token can only access specific interfaces, not all interfaces of Company A?
The problem is how to use OAuth2.0 to limit the access scope of access_token so that it can only call company A's specific interfaces (for example: obtaining mobile phone number, user's real name, user ID card), and not accessing other interfaces.
scope mechanism of OAuth2.0 perfectly solves this problem. scope is used to define access permissions for access_token. During the authorization process, we can clearly specify the permission scope of access_token through scope parameter, thereby restricting the interface it accesses.
When Company B's H5 page requests Company A's user information, Company A's authorization endpoint will request authorization from the user. scope parameter included in the request specifies the required permissions:
<code>GET /authorize? response_type=code& client_id=s6BhdRkqt3& redirect_uri=https://client.example.com/cb& scope=phone name idcard& state=xyz</code>
scope=phone name idcard means only requesting permissions to obtain the mobile phone number, user's real name and ID card.
After the user authorization, Company A issues access_tokens containing specific permissions. When Company B's H5 page uses this token to request Company A's resource server, the server will decide whether to allow access based on the permissions in the token. If the requested interface is not within the permissions scope, the server will deny access.
Therefore, scope mechanism can limit the scope of access_token usage and implement granular interface access permission control. This not only limits the access scope of access_token, but also ensures the legitimacy of interface access through user authorization, achieving dual protection.
This method clearly distinguishes the access scope of access_token and user authorization, and is an effective means to achieve fine permission control.
The above is the detailed content of How to finely control the access_token interface access permissions through the scope mechanism of OAuth2.0?. For more information, please follow other related articles on the PHP Chinese website!

Hot AI Tools

Undress AI Tool
Undress images for free

Undresser.AI Undress
AI-powered app for creating realistic nude photos

AI Clothes Remover
Online AI tool for removing clothes from photos.

Clothoff.io
AI clothes remover

Video Face Swap
Swap faces in any video effortlessly with our completely free AI face swap tool!

Hot Article

Hot Tools

Notepad++7.3.1
Easy-to-use and free code editor

SublimeText3 Chinese version
Chinese version, very easy to use

Zend Studio 13.0.1
Powerful PHP integrated development environment

Dreamweaver CS6
Visual web development tools

SublimeText3 Mac version
God-level code editing software (SublimeText3)

Hot Topics
 Using Oracle Database Integration with Hadoop in Big Data Environment
Jun 04, 2025 pm 10:24 PM
Using Oracle Database Integration with Hadoop in Big Data Environment
Jun 04, 2025 pm 10:24 PM
The main reason for integrating Oracle databases with Hadoop is to leverage Oracle's powerful data management and transaction processing capabilities, as well as Hadoop's large-scale data storage and analysis capabilities. The integration methods include: 1. Export data from OracleBigDataConnector to Hadoop; 2. Use ApacheSqoop for data transmission; 3. Read Hadoop data directly through Oracle's external table function; 4. Use OracleGoldenGate to achieve data synchronization.
 Free Korean comics online viewing free comics entrance Free Korean comics online reading free pull-down
Jun 12, 2025 pm 08:03 PM
Free Korean comics online viewing free comics entrance Free Korean comics online reading free pull-down
Jun 12, 2025 pm 08:03 PM
With the vigorous development of the Internet, Korean comics (Korean comics) have won the love of more and more readers around the world with their exquisite painting style, fascinating plots and rich and diverse themes. If you want to travel anywhere, in the exciting Korean comic world, it is crucial to find a stable, free and resource-rich online reading platform. This article will provide you with a detailed guide to watching Korean comics online for free comics, helping you easily start your Korean comic journey.
 Redis master-slave replication failure troubleshooting process
Jun 04, 2025 pm 08:51 PM
Redis master-slave replication failure troubleshooting process
Jun 04, 2025 pm 08:51 PM
The steps for troubleshooting and repairing Redis master-slave replication failures include: 1. Check the network connection and use ping or telnet to test connectivity; 2. Check the Redis configuration file to ensure that the replicaof and repl-timeout are set correctly; 3. Check the Redis log file and find error information; 4. If it is a network problem, try to restart the network device or switch the alternate path; 5. If it is a configuration problem, modify the configuration file; 6. If it is a data synchronization problem, use the SLAVEOF command to resync the data.
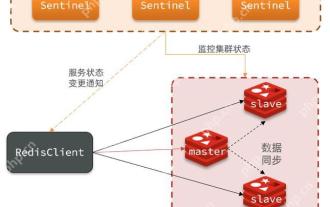 Quick location and handling of Redis cluster node failures
Jun 04, 2025 pm 08:54 PM
Quick location and handling of Redis cluster node failures
Jun 04, 2025 pm 08:54 PM
The quick location and processing steps for Redis cluster node failure are as follows: 1. Confirm the fault: Use the CLUSTERNODES command to view the node status. If the fail is displayed, the node will fail. 2. Determine the cause: Check the network, hardware, and configuration. Common problems include memory limits exceeding. 3. Repair and restore: Take measures based on the reasons, such as restarting the service, replacing the hardware or modifying the configuration. 4. Notes: Ensure data consistency, select appropriate failover policies, and establish monitoring and alarm systems.
 Kucoin appoints two high-profile executives to complete its European leadership team
Jun 12, 2025 am 10:45 AM
Kucoin appoints two high-profile executives to complete its European leadership team
Jun 12, 2025 am 10:45 AM
Global cryptocurrency exchange Kucoin recently completed the formation of its European leadership team, appointing two highly-watched executives. This personnel change is part of Kucoin’s accelerated layout in the EU market, especially in response to the upcoming cryptoasset management regulations (MICAR). Currently, the company is advancing the relevant licensing process through the Austrian Financial Markets Authority (FMA) and introducing senior experts from traditional finance and crypto to strengthen its management. KucoinEU is currently actively communicating with the FMA to achieve full compliance operations with the goal of providing a complete cryptocurrency service within the European Economic Area (EEA). At this stage, the company has not yet conducted business within the EU or EEA and is about to obtain the corresponding license.
 Performance comparison and joint application scenarios between Redis and RabbitMQ
Jun 04, 2025 pm 08:45 PM
Performance comparison and joint application scenarios between Redis and RabbitMQ
Jun 04, 2025 pm 08:45 PM
Redis and RabbitMQ each have their own advantages in performance and joint application scenarios. 1.Redis performs excellently in data reading and writing, with a latency of up to microseconds, suitable for high concurrency scenarios. 2.RabbitMQ focuses on messaging, latency at milliseconds, and supports multi-queue and consumer models. 3. In joint applications, Redis can be used for data storage, RabbitMQ handles asynchronous tasks, and improves system response speed and reliability.
 Methods and strategies to solve the problem of split brain in Redis cluster
Jun 04, 2025 pm 08:42 PM
Methods and strategies to solve the problem of split brain in Redis cluster
Jun 04, 2025 pm 08:42 PM
Effective solutions to the problem of split brain in Redis cluster include: 1) Network configuration optimization to ensure connection stability; 2) Node monitoring and fault detection, real-time monitoring with tools; 3) Failover mechanism, setting high thresholds to avoid multiple master nodes; 4) Data consistency guarantee, using replication function to synchronize data; 5) Manual intervention and recovery, and manual processing if necessary.
 Which currencies can make investors profit in the short term? How to choose? Recommended short-term profitable currency in the currency circle
Jun 12, 2025 am 11:21 AM
Which currencies can make investors profit in the short term? How to choose? Recommended short-term profitable currency in the currency circle
Jun 12, 2025 am 11:21 AM
Short-term crypto trading is risky, but it is one of the most favorable ways to make money. If you know how to apply the right strategy, the most important thing is to choose the right crypto assets, you can make a considerable profit, which is exactly what we are going to discuss today. Which currencies can make investors profit in the short term? How to choose? Recommended short-term profitable currencies in the currency circle How to choose short-term trading cryptocurrencies? Short-term transactions involve buying cryptocurrencies and holding them for a short period of time, ranging from minutes to days. This approach is both promising, risky and time-consuming as you need to constantly monitor the market. But that's not all; when choosing the right crypto assets, you should also pay attention to the following points:





